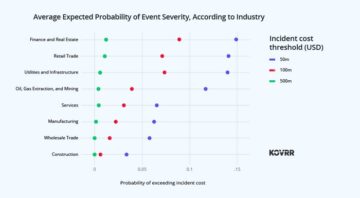
Administrators of the Python Package Index (PyPI) have removed 10 malicious software code packages from the registry after a security vendor informed them about the issue.
The incident is the latest in a rapidly growing list of recent instances where threat actors have placed rogue software on widely used software repositories such as PyPI, Node Package Manager (npm), and Maven Central, with the goal of compromising multiple organizations. Security analysts have described the trend as significantly heightening the need for development teams to exercise due diligence when downloading third-party and open source code from public registries.
Researchers at Check Point’s Spectralops.io uncovered this latest set of malicious packages on PyPI, and found them to be droppers for information-stealing malware. The packages were designed to look like legitimate code — and in some cases mimicked other popular packages on PyPI.
Malicious Code in Installation Scripts
Check Point researchers discovered that the threat actors who had placed the malware on the registry had embedded malicious code into the package installation script. So, when a developer used the “pip” install command to install any of the rogue packages, the malicious code would run unnoticed on the user’s machine and install the malware dropper.
For example, one of the fake packages, called “Ascii2text,” contained malicious code in a file (_init_.py) imported by the installation script (setup.py). When a developer attempted to install the package, the code would download and execute a script that searched for local passwords, which it then uploaded to a Discord server. The malicious package was designed to look exactly like a popular art package of the same name and description, according to Check Point.
Three of the 10 rogue packages (Pyg-utils, Pymocks, and PyProto2) appear to have been developed by the same threat actor that recently deployed malware for stealing AWS credentials on PyPI. During the setup.py installation process, Py-Utils for instance connected to the same malicious domain as the one used in the AWS credential-stealing campaign. Though Pymocks and PyProto2 connected to a different malicious domain during the installation process, their code was near identical to Pyg-utils, leading Check Point to believe the same author had created all three packages.
The other packages include a likely malware-downloader called Test-async that purported to be a package for testing code; one called WINRPCexploit for stealing user credentials during the setup.py installation process; and two packages (Free-net-vpn and Free-net-vpn2) for stealing environment variables.
“It is essential that developers are keeping their actions safe, double-checking every software ingredient in use and especially such that are being downloaded from different repositories,” Check Point warns.
The security vendor did not immediately respond when asked how long the malicious packages might have been available on the PyPI registry or how many people might have downloaded them.
Growing Supply Chain Exposure
The incident is the latest to highlight the growing dangers of downloading third-party code from public repositories without proper vetting.
Just last week, Sonatype reported discovering three packages containing ransomware that a school-age hacker in Italy had uploaded to PyPI as part of an experiment. More than 250 users downloaded one of the packages, 11 of whom ended up having files on their computer encrypted. In that instance, the victims were able to get the decryption key without having to pay a ransom because the hacker had apparently uploaded the malware without malicious intent.
However, there have been numerous other instances where attackers have used public code repositories as launching pads for malware distribution.
Earlier this year, Sonatype also discovered a malicious package for downloading the Cobalt Strike attack kit on PyPI. About 300 developers downloaded the malware before it was removed. In July, researchers from Kaspersky discovered four highly obfuscated information stealers lurking on the widely used npm repository for Java programmers.
Attackers have begun increasingly targeting these registries because of their wide reach. PyPI, for instance, has over 613,000 users and code from the site is currently embedded in more than 391,000 projects worldwide. Organizations of all sizes and types — including Fortune 500 firms, software publishers and government agencies — use code from public repositories to build their own software.