Reading Time: 6 minutesMaze creators threaten to publish the confidential data of victims unless the ransom is paid. Comodo Cyber Security team also find Equation group mutex in latest attack.
Ransomware took a sinister new turn in early 2020, evolving from a straightforward encrypt-then-extort model into a full-blown assault on a company’s data, secrets and reputation. The ‘traditional’ ransomware attack is a much-discussed model which has been covered extensively on this blog and by other publications. In brief, all files on a target system are locked with a strong encryption algorithm, and the user must pay the attacker a ransom fee to unlock them. No security software or computer expert can decrypt those files, making this one of the most dangerous attacks a company can face. Ransomware paralyses businesses who need their files for day-to-day operations and backs them into a corner where they must pay the fee or try to struggle on without access to their data.
Well, strange as it may seem, we might one day look back at ‘old ransomware’ with a sense of nostalgia and yearn for those simpler times. It seems the traditional attack was just the first steps of a criminal fraternity finding its feet with the encryption model, using it as a building block from which they can build even more effective attacks. Read on to find out why.
After a ransomware attack, some companies paid the fee to retrieve their data, but others decided to neither disclose the attack nor pay the ransom. They instead rebuilt their data from backups or by other means, and gradually got themselves back on track. It clearly annoyed the developers of Maze that some victims were simply ignoring all their hard work, so they set about creating a greater incentive for them to pay-up. This incentive came in the form of exfiltrating the company’s files and threatening to release them to the public if they didn’t pay the fee. Maze creators even went so far as to create a ‘shaming’ website which lists companies that have fallen prey to their ransomware but hadn’t yet paid the ransom.
This presents a particularly vicious double or even triple-whammy for the victim. Not only are their files inaccessible, a potentially crippling blow to organizations like hospitals and financial institutions, but now they risk their data being released to the public or sold to one of their competitors. Of course, this is an even greater headache for companies that are bound by customer-confidentiality laws. There’s also the loss of reputation and possible hit to stock-market valuation if the breach becomes public. Thirdly, if they had tried to hide the attack in the first place, they face getting swatted by regulations that require companies to disclose any breaches of this nature.
Not a pretty picture is it? Indeed, the FBI viewed Maze as such a serious threat that they issued a warning to businesses about it. With help from the Comodo Cyber Security team, this blog takes a closer look at the workings of the new Maze ransomware. One item of note off-the-top is the presence of the ‘prkMtx’ mutex object in the code. This object is used by the Equation Group’s exploitation library, ‘gPrivLibh’. For those of you who live outside the niche world of threat analytics, the Equation Group are a development team closely linked with the Stuxnet and Flame attacks. Many experts believe the group has ties to the NSA. The Maze developers obviously co-opted the mutex and put it to use in their ransomware, illustrating that ‘malware is malware’, no matter the subjective ‘good’ intentions of the original authors.
What is the Maze ransomware?
Maze ransomware, previously known as ChaCha, is distributed via malspam emails which have the malware as an attachment, via exploit kits like Spleevo and Fallout, and by cracking RDP connections that have weak passwords. Its payload is to encrypt all data on a victim’s drives with RSA-2048 encryption and the chacha20 stream cipher, then demand a ransom fee in order to decrypt the data. The image below shows the various extensions that Maze appends to encrypted files:

The malware then places a ransom message on the user’s desktop. Comodo’s researchers have identified the top 5 Maze communication servers are in Russia, Poland, Turkey, Netherlands and Austria:

Anatomy of a Maze attack
Maze is a highly sophisticated family which has strong multi-level exceptions and an anti-debugging techniques which block research teams from accessing the ransomware’s original content. The Comodo threat research team managed to overcome these barriers to unearth details not seen before.
There are three parts to the analysis:
A) IP list, web extensions and encoded URLs
B) File encryption process
C) Lock screen, decryption notes and decryption link
A) IP list, web extensions and encoded URLs
The Maze IP list includes 14 hard-coded IP addresses, indicating a wide distribution of servers. The addresses in the list are:
92.63.8.47
92.63.32.2
92.63.37.100
92.63.194.20
92.63.17.245
92.63.32.55
92.63.11.151
92.63.194.3
92.63.15.8
92.63.29.137
92.63.32.57
92.63.15.56
92.63.32.52
92.63.15.6
There are also 6 hard-coded web extensions – ‘.do’, ‘.jsp’, ‘.shtml’, ‘.html’, ‘.aspx’ and ‘.php’:

Maze uses the following URL formations (‘post/edit’ and ‘siginin/transfer’):

B) Ransomware file encryption process:
Maze creates an inventory of all files/folders on the system drive of the victim machine, and lists them in a file called ‘DECRYPT-FILES.html’:

The Comodo team checked the complexity of Maze’s encryption by running a test file through its encryption process. The file, named ‘~Test.txt’, underwent encryption involving API calls CreateFileW, ReadFile, CreateFileMappingW and MapViewOfFile:


The following screenshot shows the content of the file before encryption:

The post-encryption version and its hex dump is shown below:

C) Lock screen, decryption notes and decryption link
The Maze ransom note not only explains what has happened and how to pay, but spends a lot of time trying to ‘sell’ the payment route to the victim. The hackers seem to have realized that scary messaging and threats are a poor customer-conversion technique, and have moved onto more persuasive messaging to close the ‘sale’ earlier.
The lock screen tells the user that their files have been encrypted and touts the strength of the algorithms used. The page even encourages the user to research the algorithms in order to confirm their claims. This is presumably to accelerate payments by discouraging the user from wasting time trying to recover the files. As a dystopian sales technique, they also allow the victim to decrypt 3 files free to prove their decryptor works. The hope being that the user is more likely to pay if they have solid proof that the decryption process actually works:
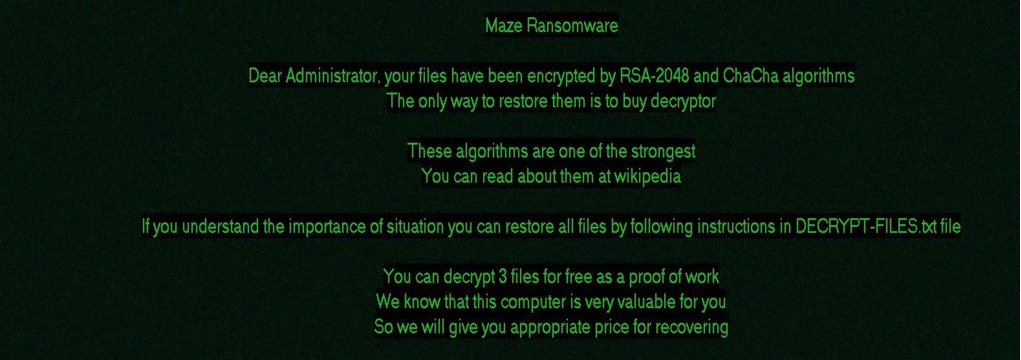
The accompanying note reiterates the severity of the situation and contains detailed instructions on how to contact the hackers to make payment. The note is clear and well laid out, borrowing the style of mainstream FAQ pages with headings like ‘What happened?’ and ‘How do I get my files back?’:

The 2nd option in the note encourages the user to visit their information website at https://mazedecrypt.top/1b010b7e5a3ebe7d. Again, the site offers proof of a slick marketing operation with soothing messages to reassure the user that payment is the correct decision. Referring to victims as ‘customers’, it purports to be an independent support site dedicated to the noble mission of saving the user’s files:

The site asks the user to upload their ‘DECRYPT-FILES.txt’ file so the hackers can identify the victim.
No charges are openly stated for the decryption, rather stage 2 of the blackmail encourages the user to contact koreadec@tutanota.com and yourealdecrypt@airmail.cc to ‘negotiate’ a price:

Ransomware Protection Software
The post Ransomware evolved – New Maze attack adds threat of data publication to existing ransomware model appeared first on Comodo News and Internet Security Information.
- "
- 11
- 2020
- a
- About
- accelerate
- access
- accessing
- addresses
- algorithm
- algorithms
- All
- analysis
- analytics
- api
- Austria
- authors
- backups
- barriers
- before
- being
- below
- Block
- Blog
- Borrowing
- breach
- breaches
- build
- Building
- businesses
- charges
- claims
- closer
- code
- Communication
- Companies
- company
- Company’s
- competitors
- computer
- Connections
- contact
- contains
- content
- create
- creates
- Creating
- creators
- Criminal
- cyber
- cyber security
- data
- day
- decided
- decision
- dedicated
- Demand
- desktop
- detailed
- details
- developers
- Development
- Display
- distributed
- distribution
- double
- drive
- dump
- Early
- Effective
- encourages
- encryption
- evolving
- existing
- expert
- experts
- Exploit
- extensions
- Face
- fallout
- family
- FAQ
- fbi
- Feet
- financial
- Financial institutions
- finding
- First
- following
- form
- Free
- from
- getting
- greater
- Group
- Group’s
- hackers
- happened
- hard work
- help
- Hide
- highly
- hope
- hospitals
- How
- How To
- HTTPS
- identify
- image
- includes
- independent
- information
- institutions
- Internet
- Internet Security
- inventory
- IP
- IP addresses
- IT
- known
- latest
- Laws
- Library
- likely
- List
- Lists
- live
- locked
- Look
- machine
- Mainstream
- make
- Making
- malware
- managed
- Marketing
- Matter
- means
- messages
- messaging
- might
- Mission
- model
- more
- most
- Nature
- Neither
- Netherlands
- news
- Notes
- Offers
- operation
- Operations
- Option
- order
- organizations
- Other
- paid
- particularly
- Passwords
- Pay
- payment
- payments
- picture
- Poland
- poor
- possible
- presence
- presents
- pretty
- price
- process
- proof
- protection
- public
- publications
- publish
- Ransom
- ransomware
- Ransomware Attack
- realized
- Recover
- regulations
- release
- released
- reputation
- require
- research
- researchers
- Risk
- Route
- running
- Russia
- sales
- saving
- Screen
- security
- sense
- serious
- set
- shown
- site
- situation
- So
- sold
- solid
- some
- sophisticated
- Stage
- stated
- stream
- strength
- strong
- style
- support
- system
- Target
- team
- teams
- techniques
- tells
- test
- The
- threats
- three
- Through
- time
- times
- top
- top 5
- track
- traditional
- Turkey
- unlock
- use
- Valuation
- various
- version
- victims
- web
- Website
- What
- WHO
- without
- Work
- works
- world









