[Bruce Land] of Cornell University will be a familiar name to many Hackaday readers, searching the site for ‘ECE4760′ will bring up many interesting topics around embedded programming. Every year [Bruce] releases yet more of the students’ work out into the wild to our great delight. This RP2040-based project is a bit more abstract than some previous work and shows yet another implementation of an older hack to utilise the DMA hardware of the RP2040 as another CPU core. While the primary focus of the RP2040 DMA subsystem is moving data between memory spaces, with minimal CPU intervention, the DMA control blocks have some fairly complex behaviour. This allows for a Turing-complete CPU to be implemented purely with the DMA hardware and a sprinkling of memory.
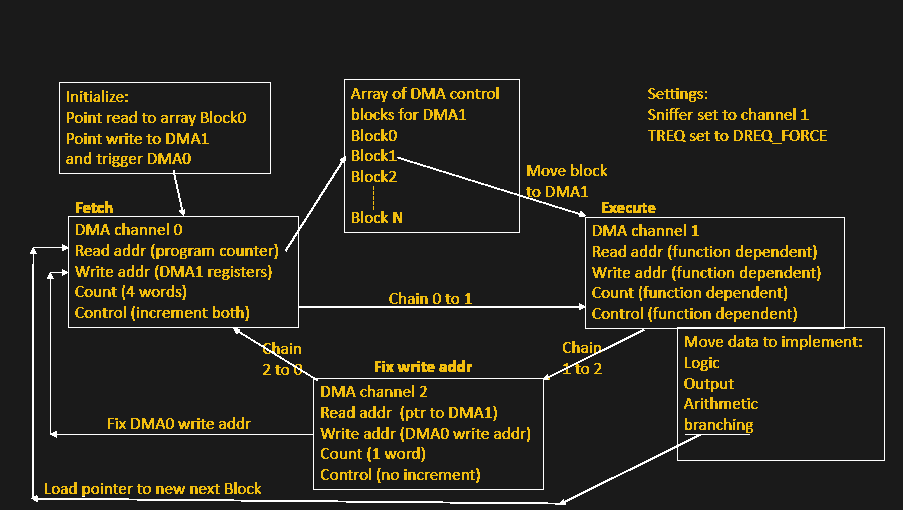
The method ties up three of the twelve DMA channels, and is estimated to have a similar performance to ‘an Arduino’ but [Bruce] doesn’t specify which one of the varied models that could be. But who cares anyway? Programming the CPU is a matter of leveraging the behaviour of the hardware, which is all memory mapped and targetable by the DMA. For example, the CPU can waggle GPIO pins by using the DMA to write values to the peripheral address space. The basic flow can be seen in the image above. DMA0 is used as the program counter, which points DMA1 to an array of DMA control blocks, a sequence of which codes for some of the ‘opcodes’ of the CPU model. DMA0 chains to (hands over control to) DMA1 which reads the control blocks and configures itself accordingly. DMA1 performs whatever data move is programmed, chains to DMA2, which in turn reprograms the DMA0 program counter to point to the next block in the list to be executed by DMA1.
By also using DMA1 to modify subsequent DMA1 control blocks (that’s self-modifying code happening there!) the system can implement more useful operations such as addition, logical operations, and conditional branching. Transport-triggered operations in certain shadow registers enable atomic set, reset, and XOR operations. All clever stuff, and a wonderful student project to have been involved with. [Bruce] points out a paper (using the Pi2) from the WOOT 2015 workshop which might offer a better explanation of this whole process.
If you’re still wondering who [Bruce Land] is and want a bit of a primer on some of these topics, then check out our previous coverage. If this theoretical stuff is a bit heavy (i.e. boring) then some of the projects have a more practical bent, such as the critical task of colour-sorting skittles.
Thumbnail image: Thomas Glau, CC BY-SA 4.0.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- Platoblockchain. Web3 Metaverse Intelligence. Knowledge Amplified. Access Here.
- Source: https://hackaday.com/2023/01/20/help-needed-on-thumb-image-rp2040-dma-hack-makes-another-cpu-core/
- a
- above
- ABSTRACT
- accordingly
- addition
- address
- All
- allows
- and
- Another
- around
- Array
- basic
- Better
- between
- Bit
- Block
- Blocks
- Boring
- bring
- Bruce
- certain
- chains
- channels
- code
- complex
- control
- could
- Counter
- CPU
- critical
- data
- delight
- dma
- Doesn’t
- embedded
- enable
- estimated
- example
- explanation
- fairly
- familiar
- flow
- Focus
- from
- great
- hack
- Hands
- Hardware
- HTML
- HTTPS
- image
- implement
- implementation
- implemented
- in
- interesting
- intervention
- involved
- itself
- Land
- leveraging
- List
- MAKES
- many
- Matter
- Memory
- method
- might
- minimal
- model
- models
- modify
- more
- move
- moving
- name
- next
- Next Block
- offer
- ONE
- Operations
- performance
- performs
- pins
- plato
- Plato Data Intelligence
- PlatoData
- Point
- points
- Practical
- previous
- primary
- primer
- process
- Program
- programmed
- Programming
- project
- projects
- purely
- readers
- registers
- Releases
- searching
- Sequence
- set
- Shadow
- Shows
- similar
- site
- some
- Space
- spaces
- Still
- Student
- subsequent
- such
- system
- Task
- The
- The Projects
- theoretical
- three
- Ties
- to
- Topics
- true
- TURN
- university
- Values
- which
- while
- WHO
- Wikipedia
- Wild
- will
- wonderful
- wondering
- Work
- work out
- write
- year
- zephyrnet