Water and wastewater utilities last week received new guidance for improving their response to cyberattacks from the US Cybersecurity and Infrastructure Security Agency (CISA), following a greater number of attacks by nation-state groups and cybercriminals targeting the underserved critical infrastructure.
CISA’s 27-page guide offered a series of important takeaways for utilities in the water sector, including detailed advice on how to create an effective incident response playbook.
The “Cyber Incident Response Guide for the Water and Wastewater Sector” aims to clarify the best practices for reporting cyber incidents, to connect utilities with resources to help improve their cybersecurity, and to encourage collaboration among the businesses in the sector. The United States has approximately 51,000 community water systems — 83% of which serve small communities accounting for only 8% of the US population — and 16,500 publicly owned treatment works for wastewater, according to CISA estimates (PDF).
Cybersecurity efforts for the water and wastewater sector (WWS), however, have been hampered by resource constraints, because utilities typically cannot pass costs on to customers and have tight budgets, says Dawn Cappelli, head of the OT-Cyber Emergency Readiness Team for industrial-cybersecurity firm Dragos.
“Most of the water utilities in the country are small, and security is not generally a focus for them,” she says. “They are under-resourced, and issues like replacing old pipes and infrastructure tend to trump cybersecurity … [and] they do not have the expertise to understand the risk posed by cyberthreats in their OT environment, which are different than those in their IT environments.”
Water & Wastewater Cybersecurity Incidents on the Rise
The US government has made securing critical infrastructure a priority following a variety of painful cyber incidents, with the water and wastewater sector becoming the latest targeted sector. In February 2021, a water utility in Oldsmar, Fla., suffered an intrusion in which the attacker tried to raise the level of a caustic chemical more than 100-fold. Six months later, cybercriminals targeted two sewage treatment plants in Maine with ransomware.
More recently, an Iranian-backed group attacked the Aliquippa Municipal Water Authority located in Pittsburgh in November, disrupting the monitoring and control systems for the water pressure to two towns. That attack turned out to be part of a spate of cyberattacks by pro-Iran assailants stretching back months that targeted various water controllers across the country.
And just this week, Veolia North America’s Municipal Water division acknowledged that ransomware actors had disrupted several of its IT systems, including those responsible for billing.
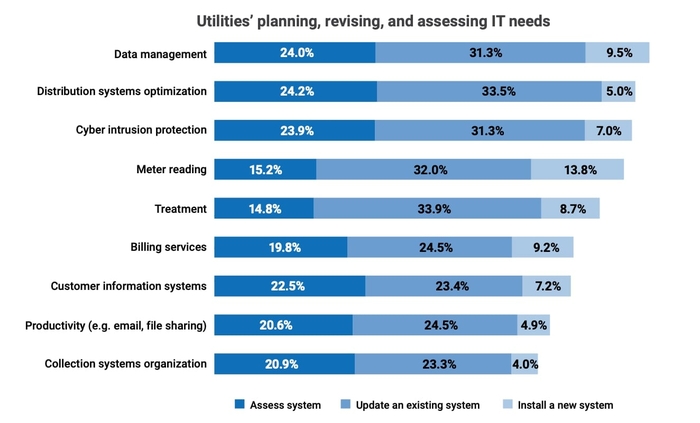
Cybersecurity ranks as the third most important IT issue for utilities. Source: American Water Works Association
While the attackers targeted the water and wastewater sector, such attacks not only affect citizens, but other critical infrastructure as well. Other sectors — such as energy and agriculture — also rely on water, says Mike Bimonte, CTO for the public sector at Armis, an attack-surface protection firm.
“These groups target small municipalities, but really, their hopes are that they have a significant impact — both downstream and upstream — on energy, health, and just the overall well being of the infrastructure,” he says, adding: “It’s … the biggest bang for the buck.”
More attacks are in the offing: “Nation-state cyber actors also have demonstrated an intent to target US WWS utilities,” CISA stated in the guide.
Improving Incident Response for the Water Sector
CISA recommends that WWS utilities plan for incidents well before they suffer a cyberattack. More than two dozen WWS organizations — along with the FBI and the Environmental Protection Agency — contributed to the guide. CISA assured utilities that the recommendations are not requirements and also warned that they are not exhaustive best practices nor include recommended technical configurations.
The guidelines call for water and wastewater utilities to do the following:
-
Prepare by creating an organizational-level incident response plan and taking part in the industry’s cyber community.
-
Improve detection capabilities and the ability to validate potential incidents to reduce noise when reporting to federal agencies.
-
Plan for containment, eradication, and recovery by sharing information with appropriate groups and have assistance lined up for remediation and mitigation.
-
Create a post-incident playbook specifying what data and evidence should be retained and distributing guidance on the lessons learned.
While the document should be a reference for all water and wastewater utilities, organizations should first plan to implement the recommendations in the “15 Cybersecurity Fundamentals for Water and Wastewater Utilities” report published by the Water Information Sharing and Analysis Center (WaterISAC), says Danielle Jablanski, a cybersecurity strategist for Nozomi Networks, an Industrial Internet of Things and operational technology security firm.
“Every asset owner has to build a strategy with their own understanding of their criticality, their technologies, their vendors, the ecosystem, their resources, and their location,” she says. “So a water utility near an Air Force base has different considerations than a water utility near Walt Disney World — they are both equally important, in my mind, but totally different considerations.”
Cyber Awareness Lacking for WWS Utilities
Getting water and wastewater utilities to prioritize cybersecurity may be difficult. Cybersecurity issues ranked No. 13 on the list of critical concerns in 2023, according to the “2023 State of the Water Industry” report published by the American Water Works Association. Fixing aging water infrastructure, ensuring the water supply, and financing capital improvements have all claimed the top 3 spots on the list of critical issues for the past five years. Cybersecurity did rank No. 10 on the list in 2022, however.
Overall, about a third of utilities (31%) plan to update existing IT systems to be more resilient to intrusion, 7% will install a new IT security system, and a quarter (24%) are assessing their cybersecurity requirements, the report stated.
The problem for water and wastewater utilities, however, is that they are regulated utilities, they are largely decentralized and autonomous, and often operate in isolated geographies, Nozomi’s Jablanski says.
Given those conditions, the sector has performed about average compared to other critical infrastructure sectors, she adds.
“The water sector is about even with other sectors who cannot pass their cybersecurity expenditures on to their customers,” Jablanski says. “That’s something we forget — a lot of companies can pass those costs on, utilities can’t.”
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://www.darkreading.com/ics-ot-security/cisa-water-sector-cyber-guide-incident-response
- :has
- :is
- :not
- $UP
- 000
- 10
- 13
- 15%
- 16
- 2021
- 2022
- 2023
- 500
- 51
- 7
- 8
- a
- ability
- About
- According
- Accounting
- acknowledged
- across
- actors
- adding
- Adds
- advice
- affect
- agencies
- agency
- Aging
- agriculture
- aims
- AIR
- Air Force
- All
- along
- also
- america
- American
- among
- an
- analysis
- and
- and infrastructure
- appropriate
- approximately
- ARE
- Armis
- AS
- Assessing
- asset
- Assistance
- Association
- assured
- At
- attack
- Attacks
- autonomous
- average
- awareness
- back
- bar
- base
- BE
- because
- becoming
- been
- before
- being
- BEST
- best practices
- Biggest
- billing
- both
- Budgets
- build
- businesses
- but
- by
- call
- CAN
- cannot
- capabilities
- capital
- Center
- Chart
- chemical
- Circle
- CISA
- Citizens
- claimed
- collaboration
- Communities
- community
- Companies
- compared
- Concerns
- conditions
- configurations
- Connect
- considerations
- constraints
- Containment
- contributed
- control
- Costs
- country
- create
- Creating
- critical
- Critical Infrastructure
- criticality
- CTO
- Customers
- cyber
- Cyberattack
- cyberattacks
- cybercriminals
- Cybersecurity
- Cybersecurity and Infrastructure Security Agency
- cyberthreats
- Danielle
- data
- decentralized
- demonstrated
- detailed
- Detection
- DID
- different
- difficult
- Disney
- distributing
- do
- document
- dozen
- ecosystem
- Effective
- efforts
- emergency
- encourage
- energy
- ensuring
- Environment
- environmental
- Environmental Protection Agency
- environments
- equally
- estimates
- Ether (ETH)
- Even
- Every
- evidence
- exhaustive
- existing
- expertise
- fbi
- February
- Federal
- financing
- Firm
- First
- five
- fla
- Focus
- following
- For
- Force
- from
- front
- Fundamentals
- generally
- geographies
- Government
- greater
- Group
- Group’s
- guidance
- guide
- guidelines
- had
- Have
- he
- head
- Health
- help
- hopes
- How
- How To
- However
- HTTPS
- ICON
- image
- Impact
- implement
- important
- improve
- improvements
- improving
- in
- incident
- incident response
- incidents
- include
- Including
- industrial
- industry
- information
- Infrastructure
- install
- intent
- Internet
- internet of things
- isolated
- issue
- issues
- IT
- it security
- ITS
- jpg
- just
- lacking
- largely
- Last
- later
- latest
- learned
- Lessons
- Lessons Learned
- Level
- like
- lined
- List
- located
- location
- Lot
- made
- May..
- mike
- mind
- mitigation
- monitoring
- months
- more
- most
- municipal
- Municipalities
- my
- Near
- networks
- New
- no
- Noise
- nor
- North
- north america
- November
- number
- of
- offered
- Offing
- often
- Old
- on
- only
- operate
- operational
- organizations
- Other
- out
- overall
- own
- owned
- owner
- painful
- part
- pass
- past
- performed
- pipes
- pittsburgh
- plan
- plants
- plato
- Plato Data Intelligence
- PlatoData
- population
- posed
- potential
- practices
- pressure
- Prioritize
- priority
- Problem
- protection
- public
- publicly
- published
- Puts
- Quarter
- raise
- rank
- ranked
- ranks
- ransomware
- Readiness
- really
- received
- recently
- recommendations
- recommended
- recommends
- recovery
- reduce
- reference
- regulated
- rely
- remediation
- report
- Reporting
- Requirements
- resilient
- resource
- Resources
- response
- responsible
- Risk
- s
- says
- sector
- Sectors
- securing
- security
- Series
- serve
- several
- sharing
- she
- should
- significant
- SIX
- Six months
- small
- So
- something
- Source
- spots
- State
- stated
- States
- Strategist
- Strategy
- such
- suffer
- supply
- system
- Systems
- T
- Takeaways
- taking
- Target
- targeted
- targeting
- team
- Technical
- Technologies
- Technology
- than
- that
- The
- their
- Them
- These
- they
- things
- Third
- this
- this week
- those
- to
- top
- TOTALLY
- towns
- treatment
- tried
- trump
- Turned
- two
- typically
- underserved
- understand
- understanding
- United
- United States
- Update
- us
- us government
- US population
- utilities
- utility
- VALIDATE
- variety
- various
- vendors
- Walt Disney
- Water
- we
- week
- WELL
- What
- when
- which
- WHO
- will
- with
- works
- world
- years
- zephyrnet