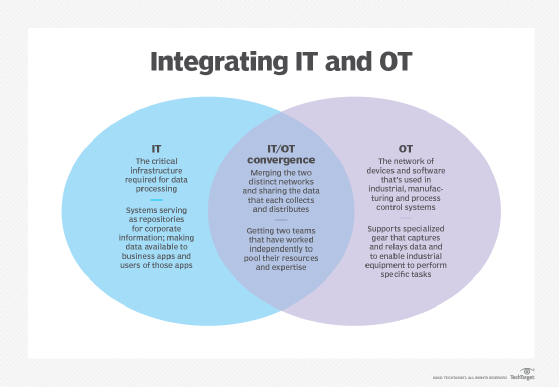
Although some companies treat information technology and operational technology as separate but equal proficiencies, most have found that there’s much to gain by converging IT and OT — enough to offset what’s often an arduous integration task.
OT’s focus is on the physical devices that control industrial operations and processes, while IT is all about data. They can run independently of each other, but there are real benefits to IT/OT convergence when each side shares its strengths, including cost and security controls.
The convergence of IT and OT is largely due to the growing adoption of internet of things (IoT) infrastructures and how IoT merges the processes and data types that OT oversees with those of traditional IT. IoT’s allure is the potential for greater efficiencies, insights and monetization opportunities that merging devices, data and people into a single environment can engender.
What is information technology?
IT is the more recognizable of these two technologies and represents the critical infrastructure required for data processing. It’s also arguably the more mature and advanced of the twin techs.
This article is part of
IT systems are data-oriented, serving as repositories for corporate information and making that data available to business-related applications and the people who use those apps. IT’s role is broad and extremely diverse, spanning systems that control and track accounting activities, sales and marketing, customer support, payroll processing and human resources management.
Physically, IT comprises the familiar components of computing systems, including servers, storage systems, network equipment and end-user devices. Most IT implementations are based on Ethernet network topologies with TCP/IP used for external data transmissions principally via the internet.
Over the past couple of decades, IT’s definition has expanded to include cloud-based services and mobile computing devices, giving IT both a local and remote presence. Connectivity to the internet is the primary enabler for IT’s remote and cloud operations and is also a primary security concern.
What is operational technology?
OT has been around for a long time, too, but it only achieved its own identity as automation was introduced to manufacturing and industrial systems, along with the need to network automated devices to gain appropriate control over factory floor devices and processes.
Today, OT refers to the network of devices and software that’s used in industrial, manufacturing and process control systems. The types of devices that hang off IoT networks run the gamut from sensors, relays and other single-purpose circuitry on shop floors to end-users’ laptops and smartphones. However, OT supports specialized gear in industrial environments that capture and relay data to enable industrial equipment to perform specific tasks. Typically, these IoT installations are referred to as industrial control systems (ICS).
Management for an ICS is often provided by supervisory control and data acquisition (SCADA) software, which handles some of the data gathering and processing, as well as monitoring equipment.
Unlike IT, which tends to turn over gear and update firmware frequently, OT devices can be put in place and left to function for many years. So as long as they are doing their jobs properly, they might not be updated regularly. That scenario often leads to situations where OT must manage several versions of a sensor operating system or application software, further complicating the already tough task of managing hundreds or thousands of endpoints.
One of the key challenges of OT is dealing with the sheer number of remote devices, which makes it essential to decentralize some processes to avoid data center bottlenecks.
The data gathered by OT systems — particularly in IoT environments — might have dual functionality. Its primary role is to ensure that the equipment being monitored by sensors continues to operate in a safe and efficient manner. But OT networks might also need to transmit that operational data back to a central site — a data center or a cloud computing service — for additional analysis in conjunction with other data already collected by IT systems.
OT vs. IT: Key differences
OT and IT are both network-based technical structures that link hundreds or thousands of pieces of equipment together, but beyond that basic topology, there are more dissimilarities than common features.
Even the networks bear distinguishing differences. IT networks typically run atop a handful of standardized OSes, including Windows and Linux. Industrial internet of things environments supporting OT might run on the IT network OSes, but there are also a number of proprietary OSes that tend to be more role-based and are often tailored to a specific industry or industrial processes. In some cases, companies will modify an off-the-shelf OS to develop one that fits their unique needs.
The communication protocols that IT and OT infrastructures use can vary as well. As noted, the majority of IT networks are Ethernet-based, whether connected by cable — copper or optical — or wireless. All or part of an OT network can also use Ethernet as its protocol, but because a single IoT implementation can potentially cover a much wider geographic area than an IT network, other protocols are used, such as LTE — mostly 4G, with 5G adoption growing — and low-power wide-area network communications in a number of implementations, including narrowband IoT and Lora.
Those non-Ethernet protocols and carriers are often used to connect the remote devices to edge servers and edge storage before tapping into the organization’s Ethernet infrastructure or a cloud service to store the collected data in a more centralized location.
Although both OT and IT networks are effectively conduits for data transfer, the size of the data packets and the speed with which they’re transmitted, analyzed and used are different. IT systems are based on block-, file- or object-oriented file systems, which means they must sustain acceptable access performance for a variety of data types that can range significantly in size and format. The data transmitted over an OT network might be extremely small — even just a few bits at a time that easily describe an aspect of a piece of gear’s current state.
OT is more device-focused than IT and uses data in real time to monitor and control physical devices — in some cases, exercising that control instantaneously to ensure that processes are running correctly without interruption and that worker safety systems aren’t compromised.
IT is user- and data-centric and often uses historical data for analyses related to customer support, back-office reporting and marketing. Generally, IT admins are more attentive to a security risk that could jeopardize the data than to the physical well-being of its users.
What is IT/OT convergence?
In its simplest terms, IT/OT convergence involves merging the two distinct networks and sharing the data that each network collects and distributes. In the real world, however, convergence is often a difficult and time-consuming process that involves getting two teams that have worked independently to pool their resources and expertise. Although there’s some overlap when it comes to skill sets, there are still plenty of processes unique to each discipline, so cross-training is needed.
Convergence is also about sharing data and strengthening security. A lot of the machine and process-related data that OT systems collect can be useful to the external-facing side of the business for forecasting, planning, supply chain control and other decision-making processes. Conversely, the OT environment can use IT-hosted business data to adjust production systems for greater efficiency.
Many companies embark on convergence to enhance their security processes. That effort often involves finding ways to adopt traditional IT security measures to the device-oriented IoT environment that OT supports. There also might be security measures in place specifically designed to protect OT’s endpoint devices, so those methods and processes must be integrated with IT security. IoT security can be particularly tricky given the number and types of devices that are connected to the network — increasing the potential attack surface.
Benefits of converging IT and OT
The chief benefit of convergence is cost. Maintaining two separate networks is an expensive proposition. By merging networks, it’s possible to reduce the amount of required networking gear, as some parts of the converged network will end up doing double duty, serving both the industrial and front-office sides of a business.
A converged physical network also makes data sharing much easier, which, as noted, can benefit the processes running on both sides of the business. But it can also mean that data can be acted on more immediately, and data storage resources can be combined for an additional economic benefit. IT and the business units it supports will be smarter when OT’s real-time data is incorporated into their data sets for enhanced analysis, enabling practices such as just-in-time manufacturing and smarter supply chain management.
The OT staff can combine sales and marketing data from IT with the voluminous data it collects to control manufacturing processes more efficiently. That way, the production of products that sell best can be ramped up, while the manufacture of less popular products can be cut back.
Although there are opportunities for cross-training to build a converged staff, organizations might still want some staff to specialize in OT or IT issues and devices, largely because so many of the devices that populate the OT world are unfamiliar to computer experts, and the operational and health information that these devices provide might be unique or oriented to a specific industry.
With AI and machine learning becoming more prominent in applications for both OT and IT environments, it makes sense to sync their abilities to interpret and act on data more effectively. For example, TinyML is bringing machine learning capabilities to more and more IoT endpoint devices; integrating their machine learning capabilities with other AI-powered applications promises benefits for both OT and IT environments.
Connections to outside organizations have become important to both environments as well, so combining their networks and network connections can benefit them equally. For some IoT environments, such as energy distribution from power plants, outside connectivity is necessary. And traditional IT networks have long relied on remote connectivity — often via cloud-based services — to stay in touch with suppliers and customers.
From an IT perspective, convergence means drastically extending the reach of installed systems and computing resources, which could create management issues, but might also present new opportunities for business expansion.
Overcome the obstacles to IT/OT convergence
IT/OT convergence is a significant challenge that involves altering procedures for both technical disciplines. Some of the obstacles that organizations must address include:
- Scale of connectivity. OT typically connects far more devices than an IT network. The sheer number of devices involved in a convergence effort must be considered before networks converge.
- Device inventory. Everything that’s connected to OT and IT networks must be accounted for to ensure that devices aren’t left unsecured or orphaned. Communication between diverse devices must be tested and confirmed. This also suggests that IT and OT personnel develop a basic understanding of the operation of each other’s equipment to enhance troubleshooting and remediation efforts.
- Firmware and other updates. As part of its security efforts, IT tends to emphasize firmware and system software updates to help ensure that no vulnerabilities are exposed. OT, on the other hand, might host devices that have been used for many years and might have out-of-date software — or might no longer be supported. Those issues must be resolved to ensure that endpoint devices don’t present additional vulnerabilities.
- Encryption. The converged systems should encrypt all communications between devices and other processing resources, whether they are internal to the organization or provided by outside services.
- Adjust networking systems for different types of data and transmission rates. Systems are often tuned to the types of data they collect and transmit. For example, OT data is typically very small and voluminous, while IT data can range from small files to huge media files. Some tuning of network devices might be required as data is bound to travel more and get mingled more frequently across a converged OT/IT environment.
- Hybrid storage systems. In most cases, the data collected in OT and IT environments will be merged at some point. Combining edge storage with more traditional centralized storage can pose problems because of the differing natures of the data each environment supports. Differences in network bandwidth, types of data, capacities, frequency of access and rates of data ingestion must all be resolved. IT groups that have limited experience with cloud storage will have to deal with a steep learning curve as IoT endpoint storage often relies on the proximity of a cloud storage service for storing data.
- Ask for a software bill of materials. SBOM is a list of all the software components and dependencies that go into a device deployed in an IoT environment. Providing SBOMs is a newer practice by product vendors, but it’s a key step in addressing issues related to the variety and age of IoT devices.
IT/OT convergence cybersecurity considerations
There are plenty of hurdles for IT and OT teams to overcome as they converge their domains, but the greatest challenge is ensuring that both environments are effectively secured and well-prepared to deal with cyberthreats.
For IT, security activities typically focus on the network infrastructures that transport data and the storage and memory systems where applications and data reside either permanently or transiently. OT must also secure all of those components, but that task is multiplied by the sheer number of endpoint devices that connect to operations networks.
Securing a converged environment requires adjustments for both OT and IT security teams to avoid any significant periods of system downtime.
In OT environments the challenge is often identifying all of the endpoints, which can be complicated by a mix of legacy and new devices with varying needs for patches and updates. So, job one might be using management software to establish an accurate inventory of devices and methodically updating them as needed. That’s a tough enough assignment by itself, but it can be further exacerbated by a variety of endpoint devices, such as cameras, sound recording equipment and sensors.
A converged system incorporates multiple data paths, including corporate server-based networks and edge devices to collection points that can be central or satellite data centers or cloud services. Understanding the nature of the data being transmitted and its purpose is also critical to securing a converged network environment. While IT might concentrate on battening down data and detecting any attempts to infiltrate the network, the OT security staff might be more concerned with anomaly detection to determine if endpoint devices have been compromised with spurious data that might cause them to function improperly or unsafely.
Backing up data is a crucial part of security and maintaining business processes to avoid disruptions for both IT and OT, but location and nature of the data that must be protected differs. Backup and disaster recovery applications and processes must be able to work effectively for both environments and must be able to efficiently access and back up an assortment of endpoint storage devices.
In a converged world, security should be bolstered by modern firewall technologies such as web application firewalls and VPNs that can encrypt data in motion across remote network connections and add a layer of protection against a variety of cyberattacks.
Rich Castagna has been involved with high-tech journalism for more than 20 years. Rich worked at TechTarget for 15 years, overseeing technical coverage and content creation as vice president of editorial. During his TechTarget tenure, Rich primarily covered storage and related technologies. Previous roles include executive editor of ZDNet Tech Update and CNET Enterprise; and editor in chief of Windows Systems magazine.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://www.techtarget.com/iotagenda/tip/Operational-technology-vs-information-technology-explained
- :has
- :is
- :not
- :where
- $UP
- 1
- 15 years
- 15%
- 20
- 20 years
- 27
- 49
- 5G
- 72
- 73
- 77
- a
- abilities
- Able
- About
- acceptable
- access
- accounted
- Accounting
- accurate
- achieved
- acquisition
- across
- Act
- activities
- add
- Additional
- address
- addressing
- adjust
- adopt
- Adoption
- advanced
- against
- age
- AI-powered
- All
- allure
- along
- already
- also
- Although
- amount
- an
- analysis
- analyzed
- and
- anomaly detection
- any
- Application
- applications
- appropriate
- apps
- arduous
- ARE
- AREA
- aren
- arguably
- around
- article
- AS
- aspect
- assignment
- assortment
- At
- attack
- Attempts
- Automated
- Automation
- available
- avoid
- back
- Backup
- Bandwidth
- based
- basic
- BE
- Bear
- because
- become
- becoming
- been
- before
- being
- benefit
- benefits
- BEST
- between
- Beyond
- Bill
- bits
- bolstered
- both
- Both Sides
- bottlenecks
- bound
- Bringing
- broad
- build
- business
- business processes
- but
- by
- cable
- cameras
- CAN
- capabilities
- capacities
- capture
- carriers
- cases
- Cause
- Center
- Centers
- central
- centralized
- chain
- challenge
- challenges
- chief
- Cloud
- cloud computing
- cloud services
- cloud storage
- CNET
- collect
- collected
- collection
- collects
- combine
- combined
- combining
- comes
- Common
- Communication
- Communications
- Companies
- complicated
- components
- comprises
- Compromised
- computer
- computing
- concentrate
- Concern
- concerned
- CONFIRMED
- conjunction
- Connect
- connected
- Connections
- Connectivity
- connects
- considerations
- considered
- content
- content-creation
- continues
- control
- controls
- converge
- Convergence
- converging
- conversely
- Copper
- Corporate
- correctly
- Cost
- could
- Couple
- cover
- coverage
- covered
- create
- creation
- critical
- Critical Infrastructure
- crucial
- Current
- Current state
- curve
- customer
- Customer Support
- Customers
- Cut
- cyberattacks
- Cybersecurity
- cyberthreats
- data
- Data Center
- data centers
- data processing
- data sets
- data sharing
- data storage
- deal
- dealing
- decades
- decentralize
- Decision Making
- definition
- dependencies
- deployed
- describe
- designed
- detecting
- Detection
- Determine
- develop
- device
- Devices
- differences
- different
- differing
- difficult
- disaster
- discipline
- disciplines
- disruptions
- distinct
- distribution
- diverse
- doing
- domains
- don
- double
- down
- downtime
- drastically
- dual
- due
- during
- each
- easier
- easily
- Economic
- Edge
- editor
- Editorial
- effectively
- efficiencies
- efficiency
- efficient
- efficiently
- effort
- efforts
- either
- embark
- emphasize
- enable
- enabler
- enabling
- encrypt
- end
- Endpoint
- endpoints
- energy
- engender
- enhance
- enhanced
- enough
- ensure
- ensuring
- Enterprise
- Environment
- environments
- equal
- equally
- equipment
- essential
- establish
- Ether (ETH)
- Even
- everything
- example
- executive
- expanded
- expansion
- expensive
- experience
- expertise
- experts
- explained
- exposed
- extending
- external
- extremely
- factory
- familiar
- far
- Features
- few
- File
- Files
- finding
- firewall
- fits
- Floor
- floors
- Focus
- For
- format
- found
- Frequency
- frequently
- from
- function
- functionality
- further
- Gain
- gamut
- gathered
- gathering
- Gear
- generally
- geographic
- get
- getting
- given
- Giving
- Go
- greater
- greatest
- Group’s
- Growing
- hand
- handful
- Handles
- Hang
- Have
- Health
- health information
- help
- his
- historical
- host
- How
- However
- HTTPS
- huge
- Hundreds
- Hurdles
- ICON
- ICS
- identifying
- Identity
- if
- immediately
- implementation
- implementations
- important
- in
- include
- Including
- Incorporated
- incorporates
- increasing
- independently
- industrial
- industrial equipment
- industry
- information
- information technology
- Infrastructure
- infrastructures
- insights
- installed
- instantaneously
- integrated
- Integrating
- integration
- internal
- Internet
- internet of things
- interpret
- into
- introduced
- inventory
- involved
- involves
- iot
- iot devices
- issues
- IT
- it security
- ITS
- itself
- Jeopardize
- Job
- Jobs
- journalism
- just
- Key
- laptops
- largely
- layer
- Leads
- learning
- left
- Legacy
- less
- Limited
- LINK
- linux
- List
- local
- location
- Long
- long time
- longer
- Lot
- machine
- machine learning
- magazine
- maintaining
- Majority
- MAKES
- Making
- manage
- management
- management software
- managing
- manner
- manufacturing
- many
- Marketing
- materials
- mature
- mean
- means
- measures
- Media
- Memory
- merges
- merging
- methods
- might
- mix
- Mobile
- Modern
- modify
- monetization
- Monitor
- monitored
- monitoring
- more
- most
- mostly
- motion
- much
- multiple
- multiplied
- must
- Nature
- necessary
- Need
- needed
- needs
- network
- network equipment
- network-based
- networking
- networks
- New
- newer
- no
- noted
- number
- obstacles
- of
- off
- offset
- often
- on
- ONE
- only
- operate
- operating
- operating system
- operation
- operational
- Operations
- opportunities
- optical
- or
- organization
- organizations
- OS
- ot
- Other
- Other Protocols
- outside
- over
- Overcome
- overlap
- overseeing
- own
- packets
- part
- particularly
- parts
- past
- Patches
- paths
- Payroll
- People
- perform
- performance
- periods
- permanently
- Personnel
- perspective
- physical
- Pictures
- piece
- pieces
- Place
- planning
- plants
- plato
- Plato Data Intelligence
- PlatoData
- Plenty
- Point
- points
- pool
- Popular
- pose
- possible
- potential
- potentially
- power
- power plants
- practice
- practices
- presence
- present
- president
- previous
- primarily
- primary
- problems
- procedures
- process
- processes
- processing
- Product
- Production
- Products
- prominent
- promises
- properly
- proposition
- proprietary
- protect
- protected
- protection
- protocol
- protocols
- provide
- provided
- providing
- purpose
- put
- range
- Rates
- RE
- reach
- real
- real world
- real-time
- real-time data
- recording
- recovery
- reduce
- referred
- refers
- regularly
- related
- relies
- remediation
- remote
- Reporting
- represents
- required
- resolved
- Resources
- Rich
- Risk
- Role
- roles
- Run
- running
- s
- safe
- Safety
- sales
- Sales and Marketing
- satellite
- scenario
- Section
- secure
- Secured
- securing
- security
- security measures
- sell
- sense
- sensors
- separate
- Servers
- service
- Services
- serving
- Sets
- several
- Shares
- sharing
- sheer
- Shop
- should
- side
- Sides
- significant
- significantly
- simplest
- single
- single environment
- site
- situations
- Size
- skill
- small
- smarter
- smartphones
- So
- Software
- software bill
- software components
- some
- Sound
- spanning
- specialize
- specialized
- specific
- specifically
- speed
- Staff
- standardized
- State
- stay
- steep
- Step
- Still
- storage
- store
- storing
- strengthening
- strengths
- structures
- such
- Suggests
- supervisory
- suppliers
- supply
- supply chain
- support
- Supported
- Supporting
- Supports
- Surface
- sync.
- system
- Systems
- T
- tailored
- tapping
- Task
- tasks
- teams
- tech
- Technical
- Technologies
- Technology
- TECHs
- tend
- tends
- tenure
- terms
- tested
- than
- that
- The
- their
- Them
- There.
- These
- they
- things
- this
- those
- thousands
- time
- time-consuming
- to
- together
- too
- touch
- tough
- track
- traditional
- transfer
- transmission
- transmit
- transport
- travel
- treat
- tricky
- tuned
- tuning
- TURN
- twin
- two
- types
- typically
- understanding
- unfamiliar
- unique
- units
- Update
- updated
- Updates
- updating
- use
- used
- useful
- users
- uses
- using
- variety
- vary
- varying
- vendors
- versions
- very
- via
- vice
- Vice President
- vs
- Vulnerabilities
- want
- was
- Way..
- ways
- WELL
- What
- What is
- when
- whether
- which
- while
- WHO
- wider
- will
- windows
- wireless
- with
- without
- Work
- worked
- worker
- worker safety
- world
- years
- ZDNET
- zephyrnet