Read Time: 5 minutes
Explore what part of the bridge needs security and how to implement that.
2022 was the year of bridge hacks, with 5 major hacks: Qubit, Wormhole, Ronin, Harmony and Nomad. Each protocol faced heavy losses in millions. The bridges ease the inter-chain transaction, but what is the use if we can’t keep them safe?
In this blog, we bring you different aspects of that blog and what to be aware of while building or auditing one to avoid such major hacks on bridges and create a better and more secure Web3 ecosystem.
Dissecting the bridge from a security point of view
There are different aspects of a bridge. Normally, a bridge comprises Web App, RPC, Smart Contracts, Tokens, Validators, Multisigs, and the community. We will be dealing with each of these aspects and what security-related things to look for in some of these.
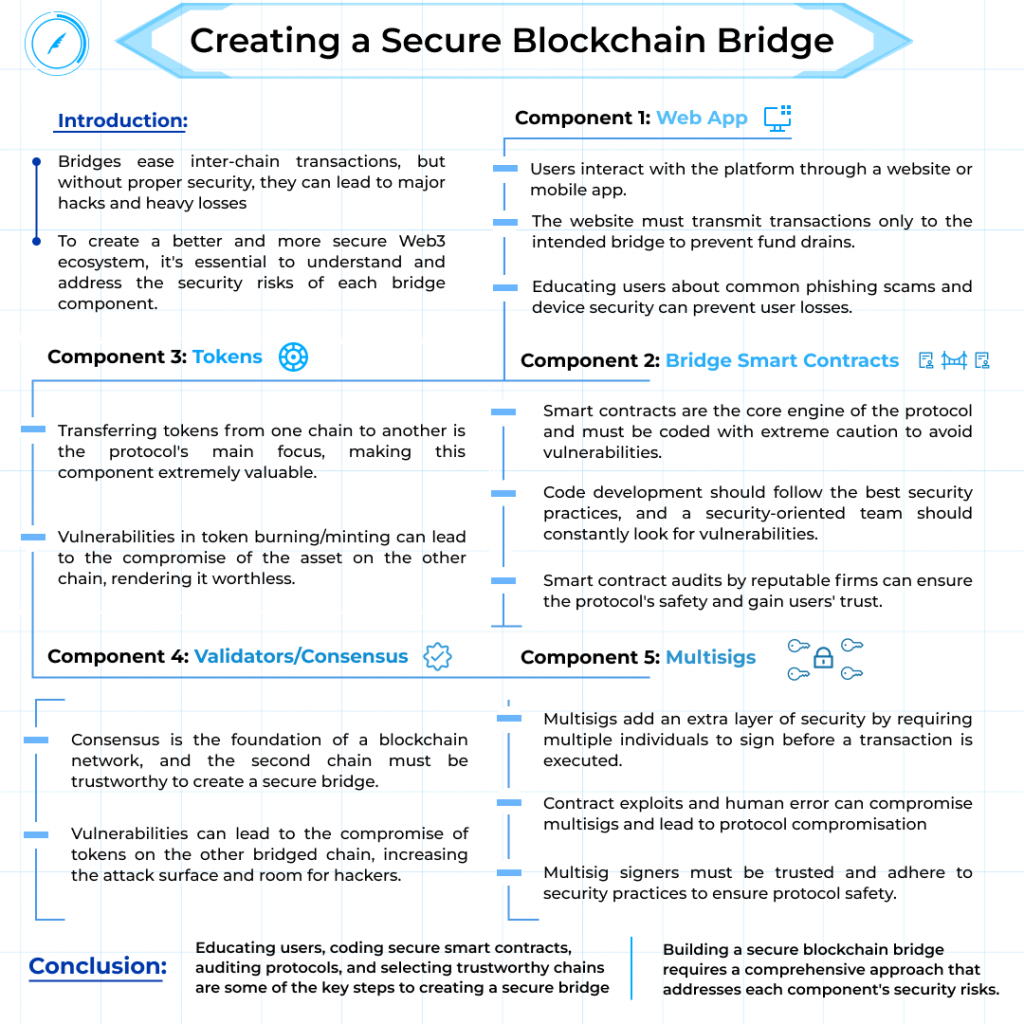
Web App
This part is where users interact with a platform for services. This can be a website or a mobile app. This is developed by the creator of the protocol or can be made by a third party for the protocol, this at a later stage interacts with the RPC(later on that) to interact with the core bridge.
The main risk area in Web App is the website itself. The Website, which acts as a platform for users to interact with the blockchain, should be transmitting the transactions only and only to the intended bridge and not some unknown contracts, which can later drain the user’s wallet. So there should be a proper check that each interaction between the platform and the blockchain should be on known contracts.
The other risk factor in Web Apps is the End-user. There needs to be more to be done to educate the user. The users often fall victim to phishing sites or have their devices infected, resulting in fund drain. To save your user from such loss protocols, consider educating them about the common mistakes users make.
Bridge Smart Contracts
Smart contracts are part of the protocol where we must be extremely cautious and constantly look for vulnerabilities while coding them. They are the core engine of the protocol. The bridge will consist of many such smart contracts, and many functionalities will likely require various contracts to interact, creating room for vulnerabilities.
Smart contracts are also visible to everyone; this is an advantage that blockchain infrastructure has transparency. Anyone can view what the protocol does and how it functions technically by going through the smart contract code, but this also means that your source code is open, and hackers can take advantage of that. Thus it is extremely important to leave your protocol with no vulnerabilities and make it safe first-hand.
The development team that writes the code for the smart contract should be a competent team that takes a security-oriented step and, at every step, asks if this code block can anyway lead to vulnerability. Are the best development practices being followed? and should always be ready in case of a security breach.
Developing secure smart contracts is a challenging task. It takes years of practice to master the craft. Thus, it is always advisable and important to go for a “Smart contract audit” from well-known firms like QuillAudits. With a team of experienced experts, QuillAudits covers every aspect of the protocol from a security point of view and leaves nothing to chance. This is one of the most crucial parameters that dictate any protocol’s success. By getting audited, the protocol gains the users’ trust by publishing a recognised firm’s audit report.
Tokens
This is the most valuable part of the protocol. Our protocol revolves around this; we are trying to transfer tokens from one chain to another, but it is more complex to handle tokens. You see, the system can have many vulnerabilities, especially when we talk about burning/minting.
One interesting thing is, in some cases, your token pool on one chain is compromised. Guess what will happen to the asset of the other chain? The asset on the other chain is unbacked and cannot be accounted for, which may make them worthless.
Validators/Consensus
Consensus represents the foundation of a blockchain network. While Ethereum and other known chains are known to be secure and tested, there can be an issue if you create a bridge for another not so tested chain.
The issue is not only compromised tokens. It can lead to the compromisation of your tokens on the other bridged chain. The second chain should be trustable to create a secure bridge. It also raises the attack surface and gives hackers room to hunt for vulnerabilities.
Multisigs
Some of the most harmful attacks on bridges in 2022 were mainly because of this part. So this is a hot topic for bridge security. The bridge is likely controlled by one or more multisigs, which are wallets that require multiple individuals to sign before the transaction gets executed.
The multisigs add an extra layer of security by not limiting the authority to a single signer but by giving voting-like rights to different signers. These multisigs can also enable the bridge contracts to be upgraded or paused.
But these are not foolproof. There are many security-related aspects to it. One of which is contract exploits, multisigs are implemented as smart contracts and thus potentially vulnerable to exploits. Many multisigs contracts have been tested for a long time and have been doing good, but the contracts are still an additional attack surface.
Human error is one of the major factors when it comes to protocol security, and the signers are people or accounts as well; thus, they can be compromised, resulting in the protocol’s compromisation, Any individual that is a signer on a multisig wallet must be trusted not to be an adversary of course, but also must be trusted to adhere to the security practices as their safety is crucial for protocol’s safety.
Conclusion
Bridges follow a complex mechanism and implementation. This complexity can open many doors for vulnerabilities and allow hackers to break the protocol. To secure the protocol from that, many measures can be taken, only some such have been discussed above, but nothing beats Auditing services.
Auditing services provide the best view and analysis of the protocol from a security point of view. Doing so can help protocols increase users’ popularity and trust and secure themselves from attacks. Thus, getting an audit before going live is always advised to avoid losses. QuillAudits has been in the game for a long time and has made a really good name for itself, Do check the website out and move through more informative blogs.
6 Views
- SEO Powered Content & PR Distribution. Get Amplified Today.
- Platoblockchain. Web3 Metaverse Intelligence. Knowledge Amplified. Access Here.
- Source: https://blog.quillhash.com/2023/04/07/part-2-bridging-the-blockchain-creating-a-secure-blockchain-bridge/
- :is
- 2022
- a
- About
- above
- Accounts
- acts
- Additional
- adhere
- ADvantage
- always
- analysis
- and
- Another
- anyone
- app
- apps
- ARE
- AREA
- around
- AS
- aspect
- aspects
- asset
- At
- attack
- Attacks
- audit
- audited
- auditing
- authority
- avoid
- BE
- because
- before
- being
- BEST
- Better
- between
- Block
- blockchain
- blockchain network
- Blog
- blogs
- breach
- Break
- BRIDGE
- bridged
- bridges
- bridging
- bring
- Building
- by
- CAN
- cannot
- case
- cases
- cautious
- chain
- chains
- challenging
- Chance
- check
- code
- Coding
- Common
- community
- competent
- complex
- complexity
- Compromised
- Consider
- constantly
- contract
- contracts
- controlled
- Core
- course
- covers
- craft
- create
- Creating
- creator
- crucial
- dealing
- developed
- Development
- Devices
- different
- discussed
- doing
- doors
- each
- ecosystem
- educate
- educating
- enable
- Engine
- error
- especially
- ethereum
- Every
- everyone
- experienced
- experts
- exploits
- extra
- extremely
- faced
- factors
- Fall
- firms
- follow
- followed
- For
- Foundation
- from
- functionalities
- functions
- fund
- Gains
- game
- getting
- gives
- Giving
- Go
- going
- good
- hackers
- hacks
- handle
- happen
- harmful
- Harmony
- Have
- heavy
- help
- HOT
- How
- How To
- HTTPS
- implement
- implementation
- implemented
- important
- in
- Increase
- individual
- individuals
- informative
- Infrastructure
- interact
- interaction
- interacts
- interesting
- issue
- IT
- itself
- Keep
- known
- layer
- lead
- Leave
- like
- likely
- live
- Long
- long time
- Look
- loss
- losses
- made
- Main
- major
- make
- many
- master
- max-width
- means
- measures
- mechanism
- millions
- mistakes
- Mobile
- Mobile app
- more
- most
- move
- multiple
- Multisig
- name
- needs
- network
- NOMAD
- normally
- of
- on
- ONE
- open
- Other
- parameters
- part
- party
- People
- phishing
- Phishing Sites
- platform
- plato
- Plato Data Intelligence
- PlatoData
- Point
- Point of View
- pool
- popularity
- potentially
- practice
- practices
- proper
- protocol
- protocol security
- protocols
- provide
- Publishing
- Qubit
- Quillhash
- raises
- ready
- recognised
- report
- represents
- require
- resulting
- rights
- Risk
- Risk Factor
- RONIN
- Room
- safe
- Safety
- Save
- Second
- secure
- security
- Services
- should
- sign
- single
- Sites
- smart
- smart contract
- Smart Contracts
- So
- some
- Source
- source code
- Stage
- Step
- Still
- success
- such
- Surface
- system
- Take
- takes
- Talk
- Task
- team
- that
- The
- the security
- their
- Them
- themselves
- These
- thing
- things
- Third
- Through
- time
- to
- token
- Tokens
- topic
- transaction
- Transactions
- transfer
- Transparency
- Trust
- trusted
- upgraded
- use
- User
- users
- validators
- Valuable
- various
- Victim
- View
- visible
- Vulnerabilities
- vulnerability
- Vulnerable
- Wallet
- Wallets
- web
- Web3
- Web3 Ecosystem
- Website
- WELL
- well-known
- What
- What is
- which
- while
- will
- with
- wormhole
- years
- Your
- zephyrnet