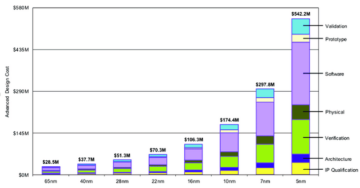
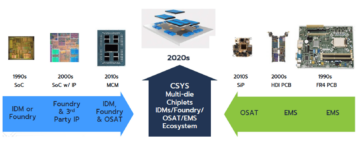
Zonal architecture in automotive design has become common in recent years in response to the increasing complexity of in-vehicle electrical systems. Automotive Ethernet is used to connect sensors and actuators to zonal gateways in ADAS (Advanced Driver Assistance Systems) enabled vehicles. With multi-gigabit links, it further connects zonal gateways to the central compute units that handle ADAS functionality and will do so for those that will handle autonomous driving capability in years to come. The in-vehicle Ethernet network is, therefore, a critical element of a car’s safety and reliability, and this blog looks at how the MACsec security protocol can be implemented in automotive SoCs to protect communications between zonal gateways.
As with regular networks, in-vehicle networks are vulnerable to several security threats such as denial-of-service attacks, man-in-the middle attacks, and unauthorized access. In contrast to regular networks, an in-vehicle network requires the unwanted behavior of the network to be detectable and handled according to both automotive safety and cybersecurity requirements. This adds additional considerations for automotive Ethernet devices, network data flow operation and network management software.
Using the IEEE802.1AE MACsec security protocol in automotive Ethernet networks mitigates most of these security threats by providing Ethernet packet data integrity protection with optional confidentiality, packet delay monitoring, detection and dropping packets from the unwanted source, as well as having a set of monitoring statistics which makes it possible to differentiate (cyber)security issues from physical layer malfunctions. Implementation of MACsec in the hardware provides the possibility to detect or filter issues at the hardware level with the minimum possible system response time, while meeting automotive safety goals. This can also be combined at a system level with handling MACsec keys using a Root of Trust/Hardware Security Module (HSM) and Device Lifecycle Management to ensure that only authorized components are used in the automotive body electronics.
MACsec-capable devices can securely communicate with each other as a group or through a set of individual MACsec connections. Depending on the application, either all traffic or part of the traffic can be protected. When combined with VLAN, MACsec allows you to separately protect different network flows within the same network. Implementing MACsec in a system requires the implementation of a MACsec control plane, a MACsec data plane and its integration into the network stack.
The Control Plane (CP) implements the MACsec secure connection management. Typically, this is the MACsec Key Agreement (MKA), which is a management protocol defined in IEEE802.1X. The CP has an API to upper-level components to receive secure connection parameters (including the long-lasting connectivity key, the CAK) and provides the connection state information. It also offers an API to control the data plane for initializing, installing, and managing secure connection(s) protected with a sequence of session keys, the SAK, which are periodically refreshed. In the MACsec standard this is called Layer Management Interface (LMI).
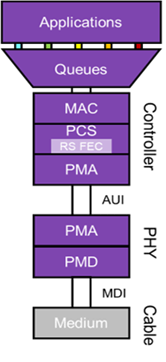
The Data Plane (DP) implements the classification, the MACsec policy and the MACsec cryptographic transform functions and provides the required packet I/O and control interfaces to integrate into the Ethernet subsystem hardware and control software. A Data Plane implementation can be software-only, software with hardware acceleration, or purely hardware-based. For the lowest latency and line-rate throughput at gigabit speeds and beyond, the data plane should be fully hardware-based. Finally, the integration binds the hardware and software components to make a full working system.
A MACsec data plane typically comes in the form of a silicon IP core to be instantiated into an automotive ASIC design for sensors, switches, gateways, MCUs, and PHY. All MACsec data plane functions should be fully in hardware to ensure key features such as line-rate throughput, minimum latency, optimal power usage and safety logic.
The Rambus MACsec-IP-361 IP core is available as a certified ISO 26262 ASIL-B Ready configuration and is designed to be a plug-and-play block for integration into the silicon architectures of automotive Ethernet MCUs, switches and sensor SoCs. It contains all necessary safety measures without a need for external safety measures, making it an ideal solution to help customers reduce development time and risk when designing a fully certified MACsec-capable SoC or ASIC.
Resources:
Maxim Demchenko
(all posts)
Maxim Demchenko is director, project manager, and lead software developer at Rambus.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://semiengineering.com/securing-automotive-ethernet-connections-with-macsec/
- :has
- :is
- 102
- 28
- 8
- a
- acceleration
- access
- According
- ADAs
- Additional
- Adds
- advanced
- Agreement
- All
- All Posts
- allows
- also
- an
- and
- api
- Application
- architecture
- ARE
- AS
- asic
- Assistance
- At
- Attacks
- authorized
- automotive
- autonomous
- available
- BE
- become
- behavior
- between
- Beyond
- Block
- Blog
- body
- both
- by
- called
- CAN
- capability
- central
- Certified
- classification
- combined
- come
- comes
- Common
- communicate
- Communications
- complexity
- components
- Compute
- confidentiality
- Configuration
- Connect
- connection
- Connections
- Connectivity
- connects
- considerations
- contains
- contrast
- control
- Core
- critical
- cryptographic
- Customers
- cyber
- Cybersecurity
- data
- defined
- delay
- Depending
- Design
- designed
- designing
- detect
- Detection
- Developer
- Development
- device
- Devices
- different
- differentiate
- Director
- do
- driver
- driving
- Dropping
- each
- either
- Electronics
- element
- enabled
- ensure
- external
- Features
- filter
- Finally
- flow
- Flows
- For
- form
- from
- full
- fully
- functionality
- functions
- further
- gateways
- Goals
- Group
- handle
- handled
- Handling
- Hardware
- having
- help
- How
- HTTPS
- ideal
- implementation
- implemented
- implementing
- implements
- in
- Including
- increasing
- individual
- information
- installing
- integrate
- integration
- integrity
- Interface
- interfaces
- into
- IP
- ISO
- issues
- IT
- ITS
- Key
- keys
- Latency
- layer
- lead
- Level
- lifecycle
- links
- logic
- LOOKS
- lowest
- make
- MAKES
- Making
- malfunctions
- management
- management software
- manager
- managing
- measures
- meeting
- Middle
- minimum
- module
- monitoring
- most
- necessary
- Need
- network
- Network Data
- networks
- of
- Offers
- on
- only
- operation
- optimal
- or
- Other
- packets
- parameters
- part
- physical
- plane
- plato
- Plato Data Intelligence
- PlatoData
- policy
- possibility
- possible
- Posts
- power
- project
- protect
- protected
- protection
- protocol
- provides
- providing
- purely
- ready
- receive
- recent
- reduce
- regular
- reliability
- required
- Requirements
- requires
- response
- Risk
- root
- s
- Safety
- same
- secure
- securely
- securing
- security
- Security threats
- sensors
- separately
- Sequence
- session
- set
- several
- should
- Silicon
- So
- Software
- software components
- solution
- Source
- speeds
- stack
- standard
- State
- statistics
- such
- system
- Systems
- that
- The
- therefore
- These
- this
- those
- threats
- Through
- throughput
- time
- to
- traffic
- Transform
- typically
- unauthorized
- units
- unwanted
- Usage
- used
- using
- Vehicles
- Vulnerable
- WELL
- when
- which
- while
- will
- with
- within
- without
- working
- years
- you
- zephyrnet