In what’s perhaps one of the most impressive laptop reverse engineering posts in recent memory, [Andrey Konovalov] brings us an incredibly detailed story of how he’s discovered and successfully enabled a USB device controller in a ThinkPad X1 Carbon equipped with a 6th gen Intel CPU.
If you ever wanted to peek at the dirty secrets of a somewhat modern-day Intel CPU-based system, this write-up spares you no detail, and spans dozens of abstraction layers — from Linux drivers and modifying NVRAM to custom USB cable building and BIOS chip flashing, digging deep into undocumented PCH registers for the dessert.
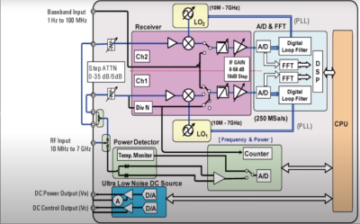
All [Andrey] wanted was to avoid tinkering with an extra Raspberry Pi. While using a PCIe connected device controller, he’s found a reference to intel_xhci_usb_sw-role-switch in Linux sysfs, and dove into a rabbit hole, where he discovered that the IP core used for the laptop’s USB ports has a ‘device’ mode that can be enabled. A dig through ACPI tables confirmed this, but also highlighted that the device is disabled in BIOS. What’s more, it turned out to be locked away behind a hidden menu. Experiments in unlocking that menu ensued, in particular when it comes to bypassing Intel Boot Guard, a mechanism that checks BIOS image signatures before boot.

[Andrey] shows us a few different ways he’s tried to enable the controller, just for the fun of it, from using BootGuard exploits to reverse-engineering NVRAM EFI variable mapping, and even a lengthy section on poking directly at the Intel PCH’s registers trying to enable the USB device peripheral from userspace, assisted by [Maxim Goryachy] of Intel reverse-engineering fame. In the end, the NVRAM patching way turned out to be the most viable way for an average user, and the blog post has more than enough detail for any enterprising hacker who would like to make it work for them as well.
As a victory dance, we get a section on all the wonderful things you can do if your device supports USB device mode. There’s the obvious USB storage example, but [Alexey] shows us a few cool tools to remember – the Raw Gadget Linux kernel framework for building any kind of USB device you could dream of, the syzkaller USB stack fuzzer, and Facedancer, a framework for USB device emulation.
If you think all of this is a lot, mind you that we have only described about half of all the cool stuff that the blog post contains — you should go check it out, and make a cup of tea, because there’s just that much cool stuff to learn about.
Genuinely, this blog post is a testament to a hacker’s dedication, and a shining example of just how far you can reach if you are willing to keep digging. Does your laptop hide some secrets that nobody knew existed? Remember, there’s only one way to find out.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://hackaday.com/2024/03/01/thinkpad-x1-carbon-turned-usb-device-through-relentless-digging/
- :has
- :is
- :where
- 1
- 210
- 420
- 6th
- 800
- a
- About
- abstraction
- All
- also
- an
- and
- any
- ARE
- AS
- assisted
- At
- average
- avoid
- away
- BE
- because
- before
- behind
- Blog
- Brings
- Building
- but
- by
- cable
- CAN
- carbon
- check
- Checks
- chip
- comes
- CONFIRMED
- connected
- Connected Device
- contains
- controller
- Cool
- Core
- could
- CPU
- Cup
- custom
- dance
- dedication
- deep
- described
- detail
- detailed
- device
- different
- DIG
- directly
- disabled
- discovered
- do
- does
- dove
- dozens
- dream
- drivers
- ease
- enable
- enabled
- end
- Engineering
- enough
- enterprising
- equipped
- Even
- EVER
- example
- existed
- experiments
- exploits
- extra
- FAME
- far
- few
- Find
- flashing
- For
- found
- Framework
- from
- fun
- Gen
- get
- got
- Guard
- hacker
- Half
- Have
- he
- Hidden
- Highlighted
- Hole
- How
- HTTPS
- if
- image
- impressive
- in
- incredibly
- Intel
- into
- IP
- IT
- jpg
- just
- Keep
- Kind
- knew
- laptop
- layers
- LEARN
- like
- linux
- locked
- Lot
- make
- mapping
- max-width
- Maxim
- mechanism
- Memory
- Menu
- mind
- Mode
- more
- most
- much
- no
- nobody
- obvious
- of
- on
- ONE
- only
- out
- particular
- Patching
- perhaps
- peripheral
- plato
- Plato Data Intelligence
- PlatoData
- ports
- Post
- Posts
- Rabbit
- Raspberry
- Raspberry Pi
- Raw
- reach
- recent
- reference
- registers
- relentless
- remember
- reverse
- secrets
- Section
- shining
- should
- Shows
- Signatures
- some
- somewhat
- spans
- stack
- storage
- stuff
- Successfully
- Supports
- system
- Tea
- testament
- than
- that
- The
- Them
- things
- Think
- this
- Through
- to
- tools
- tried
- trying
- Turned
- unlock
- unlocking
- us
- usb
- used
- User
- using
- variable
- viable
- victory
- wanted
- was
- Way..
- ways
- we
- WELL
- when
- while
- WHO
- willing
- with
- wonderful
- Work
- would
- x1
- you
- Your
- zephyrnet