Read Time: 6 minutes
Web3 being one of the latest technology advancements to take the internet by storm, Web3 is very vibrant in terms of research and new innovations in the field of decentralised systems and distributed networks. Multi-Party Computation exemplifies how versatile the blockchain can be in incorporating new advancements. In this blog, we will discuss what Multi-Party Computation is, what use case it is finding in the blockchain industry, and how it is making Web3 more secure and safe. Let’s start by understanding what Multi-Party Computation is.
What is Multi-Party Computation?
Multi-Party Computation is a cryptographic protocol dealing with Privacy-Preserving Technologies. MPC is used by more than one party to collectively arrive at a result or conclusion drawn from their personal data such that no party has access to the data of any other party, and still, the purpose is served. This is possible by providing each participating party with private data fragments to participate in computing a specific result.
If we try to understand the above statement in simple terms, MPC brings together different parties holding different bits of information which, when combined and done some computation on generates a result or action like revealing a secret, signing a message or approving a transaction, The two main cautious parameters to focus on while implementing the MPC is:-
- If any party reveals or shows its secret information to another party, then this dishonest party should not be able to influence the result of the computation.
- Secure multi-party computation. There should be no way that the secret information held by each party gets disclosed due to whatever reason or any logical flaw in the implementation. If it happens, the whole reason for MPC gets beaten.
How does Multi-Party Computation work?
Let’s imagine this, you are having lunch with your colleagues, and now you wonder what is the average salary of your group. Still, you do not want to disclose your salary to others, nor would the others like to disclose the salary to you. How can we proceed with this so that we find out the average salary without knowing the salary of any one person?
Let’s take a multi-party computation example. There are 4 of you (P1, P2, P3, P4) whose actual salaries are (a,b,c,d). What we can do is we can select random numbers such that their sum equals the actual salary of any person, basically what that means is choose 4 any 4 numbers such that their sum is “a”, “a” = “a1” + “a2” + “a3” + “a4”, now distribute these a1,a2,a3,a4 to the persons P1, P2, P3, P4 so P1 knows a1, P2 knows a2, P3 knows a3, P4 knows a4, when we do this for every person, each person has 4 values like P1 has a1,b1,c1,d1, P2 has a2,b2,c2,d2 and so on… The point is none of them knows anything about the other salary, and no one knows all the 4 parameters of any other person. Now when they come together and tell the sum of the assigned values, it will sum out to be a1+b1+c1+d1+a2+b2+c2+d2+a3+b3+c3+d3+a4+b4+c4+d4 which is equal to the sum of total of their all salaries which when divided by 4 will give the average.
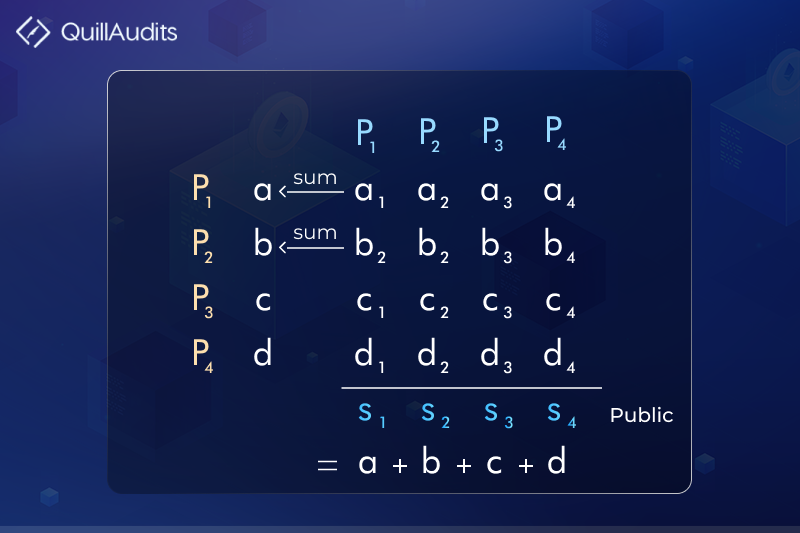
This was how you could calculate the average of 4 salaries without the other people knowing the salary of any other in the group. This is one such example we can use Multi-Party computation to keep information private and calculate results and objectives.
How can MPC improve Web3 security?
Now that we understand what secure multi-party computation is and how it works, it’s time we learn about different possible applications of MPC in Web3 and how it helps secure Web3 from some of the attacks and vulnerabilities out there. Let’s go through some of them one by one.

Protecting Identity Wallets
2022 was the year of bridge hacks. We saw a huge spike in the bridge hacks, and some of the biggest bridge hacks were due to the compromisation of the signer’s keys. You see, these keys represent the identity and credibility of the person. If they are compromised, it’s a straight bye-bye to your funds.
MPC has the potential to save our protocols and bridges from being hacked by the compromisation of the private keys, by sharding of keys and reconstructing them dynamically by combining the input of all parties is an awesome way of protecting the protocols. Even if one party is compromised, the blockchain transaction won’t be signed, and we can enjoy the security.
There are many platforms which are emerging as MPC wallet providers which have a business model around providing mpc wallet as a service. We might see this use case coming into the mainstream soon.
Transaction Privacy and Confidentiality
The core foundation of blockchain is the Distributed Ledger Technology(DLT) and data on the chain so that all the nodes and validators have the conformity of the integrity and authenticity and authorisation of the data, but what if you need the security and abilities of the blockchain, but you do not want to keep the data public to stay Database it can be confidential, do we have any solution for that?
MPC provides one of the best solutions for these problems. Such transactions can be offloaded from the blockchain and processed via MPC, and the transaction receipt can be captured over the blockchain, which can act as proof.
High-Value Transactions
There are numerous different protocols and arrangements which require the permission of different parties, or we can call them signs of different parties to execute a task, an action, or a transaction. MPC, whose main basis is to form a final result by taking in confidential data, is a perfect for such cases. On the blockchain, we can do this by taking in the input from different parties and then signing the transaction.
An alternative for this is multi-sig, but lately, we have seen bridge hacks which were possible in the first place due to flaws in the multi-sig method, and now it’s time we try the MPC methods. MPC vs Multisig is another interesting part, but out of this blog’s scope, let’s take it in another blog.
Conclusion
We have seen the advantages and how the MPC can fuel the security need of Web3 protocols. MPC is one of the promising solutions and alternatives to some issues in the current Web3 scenario.
Apart from MPC, if we look at Web3 as a whole, in the last few years, we have been noticing a continuous rise in the number of attacks in the Web3 world, which suggest the need for strengthening blockchain security only then we can look for Web3 centric future and to make that future a reality the security must be in the hands of the experts. Smart Contracts Audits are the only way to guarantee a security-oriented future, and QuillAudits is one of the leading players in the field. Visit our website to get your protocol audited and help make Web3 a safer place
18 Views
- SEO Powered Content & PR Distribution. Get Amplified Today.
- Platoblockchain. Web3 Metaverse Intelligence. Knowledge Amplified. Access Here.
- Source: https://blog.quillhash.com/2023/04/11/why-multi-party-computation-mpc-is-critical-for-web3-security/
- :is
- a
- abilities
- Able
- About
- above
- access
- Act
- Action
- advancements
- advantages
- All
- alternative
- alternatives
- and
- Another
- applications
- ARE
- around
- AS
- assigned
- At
- Attacks
- audited
- audits
- authenticity
- authorisation
- average
- Basically
- basis
- BE
- being
- BEST
- Biggest
- blockchain
- blockchain industry
- Blockchain security
- Blog
- BRIDGE
- bridges
- Brings
- business
- business model
- by
- calculate
- call
- CAN
- case
- cases
- cautious
- chain
- Choose
- colleagues
- collectively
- combined
- combining
- come
- coming
- Compromised
- computation
- computing
- conclusion
- continuous
- contracts
- Core
- could
- Credibility
- critical
- cryptographic
- Current
- data
- Database
- dealing
- decentralised
- different
- Disclose
- discuss
- dishonest
- distribute
- distributed
- Distributed Ledger
- divided
- DLT
- drawn
- dynamically
- each
- Each person
- emerging
- enjoy
- Equals
- Even
- Every
- example
- execute
- exemplifies
- experts
- few
- field
- final
- Find
- finding
- First
- flaw
- flaws
- Focus
- For
- form
- Foundation
- from
- Fuel
- funds
- future
- generates
- get
- Give
- Go
- Group
- guarantee
- hacked
- hacks
- Hands
- happens
- Have
- having
- Held
- help
- helps
- holding
- How
- HTTPS
- huge
- Identity
- implementation
- implementing
- improve
- in
- incorporating
- industry
- influence
- information
- innovations
- input
- integrity
- interesting
- Internet
- issues
- IT
- ITS
- Keep
- keys
- Knowing
- Last
- latest
- leading
- LEARN
- Ledger
- like
- logical
- Look
- lunch
- Main
- Mainstream
- make
- Making
- many
- max-width
- means
- message
- method
- methods
- might
- model
- more
- MPC
- multi-party
- Multisig
- Need
- networks
- New
- nodes
- number
- numbers
- numerous
- objectives
- of
- on
- ONE
- Other
- Others
- parameters
- part
- participate
- participating
- parties
- party
- People
- perfect
- permission
- person
- personal
- personal data
- persons
- Place
- Platforms
- plato
- Plato Data Intelligence
- PlatoData
- players
- Point
- possible
- potential
- privacy
- private
- Private Keys
- problems
- promising
- proof
- protecting
- protocol
- protocols
- providers
- provides
- providing
- public
- purpose
- Quillhash
- random
- Reality
- reason
- represent
- require
- research
- result
- Results
- revealing
- Reveals
- Rise
- safe
- safer
- salaries
- salary
- Save
- scenario
- scope
- Secret
- secure
- security
- service
- sharding
- should
- Shows
- signed
- signing
- Signs
- Simple
- smart
- Smart Contracts
- So
- solution
- Solutions
- some
- Soon
- specific
- spike
- start
- Statement
- stay
- Still
- Storm
- straight
- strengthening
- such
- Systems
- Take
- taking
- Task
- Technologies
- Technology
- terms
- that
- The
- the security
- their
- Them
- There.
- These
- Through
- time
- to
- together
- Total
- transaction
- Transactions
- understand
- understanding
- use
- use case
- validators
- Values
- versatile
- via
- vibrant
- Visit
- vs
- Vulnerabilities
- Wallet
- Way..
- Web3
- Web3 world
- Website
- What
- What is
- which
- while
- will
- with
- without
- Work
- works
- world
- would
- year
- years
- Your
- zephyrnet