1University of California, Berkeley, USA.
2QuSoft and Centrum Wiskunde & Informatica, The Netherlands.
3Department of Applied Mathematics and Computer Science, Technical University of Denmark, Denmark.
4Computing and Mathematical Sciences, Caltech, USA.
Find this paper interesting or want to discuss? Scite or leave a comment on SciRate.
Abstract
Copy-protection allows a software distributor to encode a program in such a way that it can be evaluated on any input, yet it cannot be “pirated” – a notion that is impossible to achieve in a classical setting. Aaronson (CCC 2009) initiated the formal study of quantum copy-protection schemes, and speculated that quantum cryptography could offer a solution to the problem thanks to the quantum no-cloning theorem. In this work, we introduce a quantum copy-protection scheme for a large class of evasive functions known as “compute-and-compare programs” – a more expressive generalization of point functions. A compute-and-compare program $mathsf{CC}[f,y]$ is specified by a function $f$ and a string $y$ within its range: on input $x$, $mathsf{CC}[f,y]$ outputs $1$, if $f(x) = y$, and $0$ otherwise. We prove that our scheme achieves non-trivial security against fully malicious adversaries in the quantum random oracle model (QROM), which makes it the first copy-protection scheme to enjoy any level of provable security in a standard cryptographic model. As a complementary result, we show that the same scheme fulfils a weaker notion of software protection, called “secure software leasing”, introduced very recently by Ananth and La Placa (eprint 2020), with a standard security bound in the QROM, i.e. guaranteeing negligible adversarial advantage. Finally, as a third contribution, we elucidate the relationship between unclonable encryption and copy-protection for multi-bit output point functions.
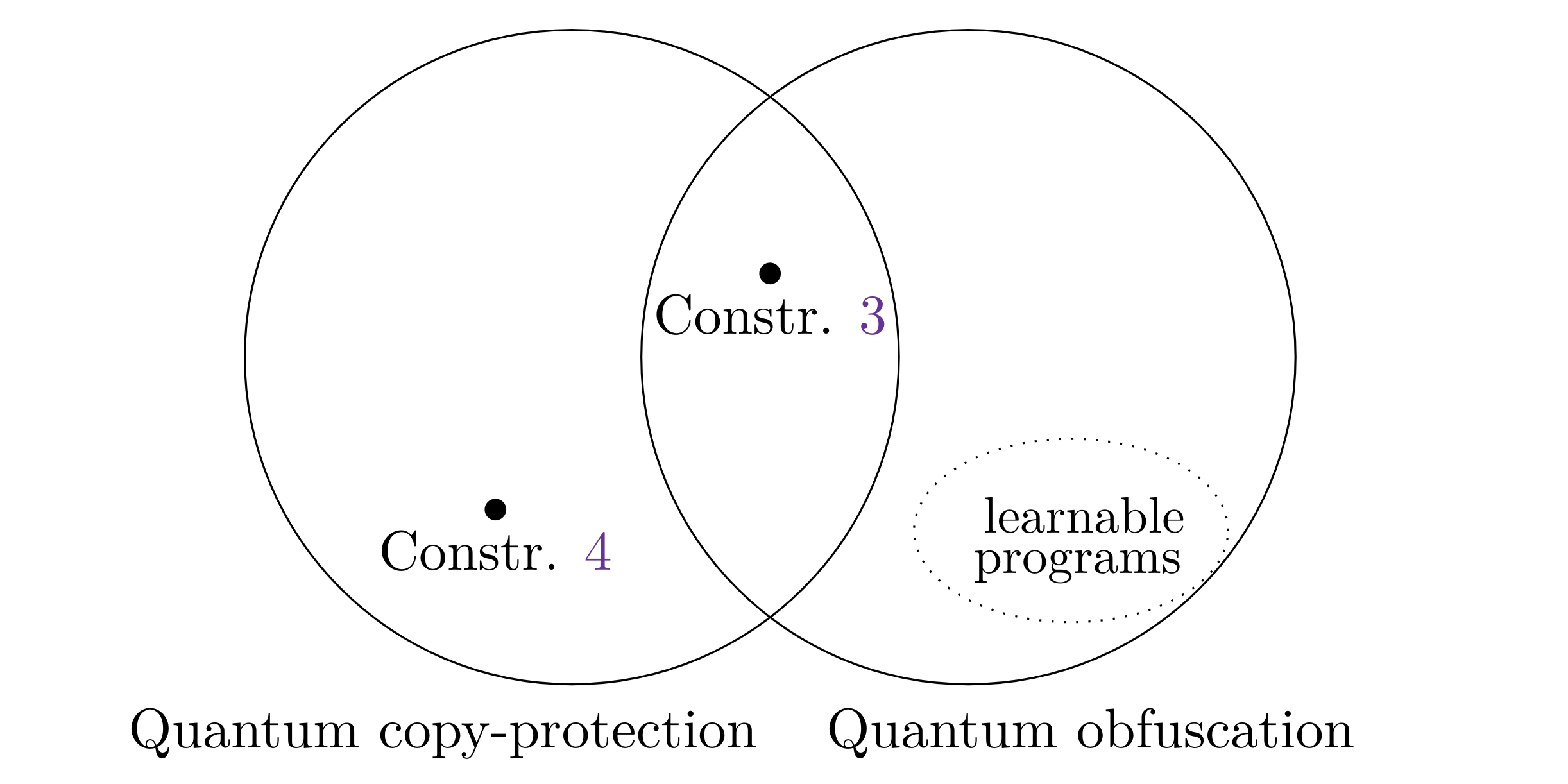
Featured image: Separation between quantum copy-protection and quantum virtual black-box obfuscation. Construction #3 features a quantum copy-protection scheme for point functions which satisfies both notions, while our second scheme for compute-and-compare programs in Construction #4 does not satisfy the notion of quantum virtual black-box obfuscation. Finally, while learnable programs can be trivially obfuscated, they can never be copy-protected.
Popular summary
► BibTeX data
► References
[1] Scott Aaronson. Limitations of quantum advice and one-way communication. Theory of Computing, 1 (1): 1–28, 2005. ISSN 1557-2862. 10.4086/toc.2005.v001a001. URL http://dx.doi.org/10.4086/toc.2005.v001a001.
https://doi.org/10.4086/toc.2005.v001a001
[2] Scott Aaronson. Quantum copy-protection and quantum money. In 2009 24th Annual IEEE Conference on Computational Complexity, pages 229–242, 2009. 10.1109/CCC.2009.42.
https://doi.org/10.1109/CCC.2009.42
[3] Scott Aaronson, Jiahui Liu, Qipeng Liu, Mark Zhandry, and Ruizhe Zhang. New approaches for quantum copy-protection. In Tal Malkin and Chris Peikert, editors, Advances in Cryptology – CRYPTO 2021, pages 526–555, Cham, 2021. Springer International Publishing. ISBN 978-3-030-84242-0. 10.1007/978-3-030-84242-0_19.
https://doi.org/10.1007/978-3-030-84242-0_19
[4] Gorjan Alagic and Bill Fefferman. On quantum obfuscation. CoRR, abs/1602.01771, 2016. URL http://arxiv.org/abs/1602.01771.
arXiv:1602.01771
[5] Gorjan Alagic, Christian Majenz, Alexander Russell, and Fang Song. Quantum-access-secure message authentication via blind-unforgeability. In Anne Canteaut and Yuval Ishai, editors, Advances in Cryptology – EUROCRYPT 2020, pages 788–817, Cham, 2020. Springer International Publishing. ISBN 978-3-030-45727-3. 10.1007/978-3-030-45727-3_27.
https://doi.org/10.1007/978-3-030-45727-3_27
[6] Andris Ambainis, Mike Hamburg, and Dominique Unruh. Quantum security proofs using semi-classical oracles. In Annual International Cryptology Conference, pages 269–295. Springer, 2019. 10.1007/978-3-030-26951-7_10.
https://doi.org/10.1007/978-3-030-26951-7_10
[7] Prabhanjan Ananth and Rolando L. La Placa. Secure software leasing. In Anne Canteaut and François-Xavier Standaert, editors, Advances in Cryptology – EUROCRYPT 2021, pages 501–530, Cham, 2021. Springer International Publishing. ISBN 978-3-030-77886-6. 10.1007/978-3-030-77886-6_17.
https://doi.org/10.1007/978-3-030-77886-6_17
[8] Prabhanjan Ananth, Fatih Kaleoglu, Xingjian Li, Qipeng Liu, and Mark Zhandry. On the feasibility of unclonable encryption, and more, 2022. URL https://doi.org/10.1007/978-3-031-15979-4_8.
https://doi.org/10.1007/978-3-031-15979-4_8
[9] Boaz Barak, Oded Goldreich, Russell Impagliazzo, Steven Rudich, Amit Sahai, Salil Vadhan, and Ke Yang. On the (im) possibility of obfuscating programs. Journal of the ACM (JACM), 59 (2): 1–48, 2012. 10.1007/3-540-44647-8_1.
https://doi.org/10.1007/3-540-44647-8_1
[10] Mihir Bellare and Phillip Rogaway. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, CCS ’93, page 62–73, New York, NY, USA, 1993. Association for Computing Machinery. ISBN 0897916298. 10.1145/168588.168596. URL https://doi.org/10.1145/168588.168596.
https://doi.org/10.1145/168588.168596
[11] Charles H. Bennett, Ethan Bernstein, Gilles Brassard, and Umesh Vazirani. Strengths and weaknesses of quantum computing. SIAM J. Comput., 26 (5): 1510–1523, October 1997. ISSN 0097-5397. 10.1137/S0097539796300933. URL https://doi.org/10.1137/S0097539796300933.
https://doi.org/10.1137/S0097539796300933
[12] Nina Bindel, Mike Hamburg, Kathrin Hövelmanns, Andreas Hülsing, and Edoardo Persichetti. Tighter proofs of cca security in the quantum random oracle model. In Dennis Hofheinz and Alon Rosen, editors, Theory of Cryptography, pages 61–90, Cham, 2019. Springer International Publishing. ISBN 978-3-030-36033-7. 10.1007/978-3-030-36033-7_3.
https://doi.org/10.1007/978-3-030-36033-7_3
[13] Dan Boneh, Özgür Dagdelen, Marc Fischlin, Anja Lehmann, Christian Schaffner, and Mark Zhandry. Random oracles in a quantum world. In International Conference on the Theory and Application of Cryptology and Information Security, pages 41–69. Springer, 2011. 10.1007/978-3-642-25385-0_3.
https://doi.org/10.1007/978-3-642-25385-0_3
[14] Zvika Brakerski. Quantum fhe (almost) as secure as classical. In Hovav Shacham and Alexandra Boldyreva, editors, Advances in Cryptology – CRYPTO 2018, pages 67–95, Cham, 2018. Springer International Publishing. ISBN 978-3-319-96878-0. 10.1007/978-3-319-96878-0_3.
https://doi.org/10.1007/978-3-319-96878-0_3
[15] Anne Broadbent and Sébastien Lord. Uncloneable Quantum Encryption via Oracles. In Steven T. Flammia, editor, 15th Conference on the Theory of Quantum Computation, Communication and Cryptography (TQC 2020), volume 158 of Leibniz International Proceedings in Informatics (LIPIcs), pages 4:1–4:22, Dagstuhl, Germany, 2020. Schloss Dagstuhl – Leibniz-Zentrum für Informatik. ISBN 978-3-95977-146-7. 10.4230/LIPIcs.TQC.2020.4. URL https://drops-dev.dagstuhl.de/entities/document/10.4230/LIPIcs.TQC.2020.4.
https://doi.org/10.4230/LIPIcs.TQC.2020.4
[16] Anne Broadbent, Stacey Jeffery, Sé bastien Lord, Supartha Podder, and Aarthi Sundaram. Secure software leasing without assumptions. In Theory of Cryptography, pages 90–120. Springer International Publishing, 2021. 10.1007/978-3-030-90459-3_4. URL https://doi.org/10.1007.
https://doi.org/10.1007/978-3-030-90459-3_4
[17] Alper Cakan and Vipul Goyal. Unclonable cryptography with unbounded collusions, 2023.
[18] Ran Canetti, Oded Goldreich, and Shai Halevi. The random oracle methodology, revisited. J. ACM, 51 (4): 557–594, July 2004. ISSN 0004-5411. 10.1145/1008731.1008734. URL https://doi.org/10.1145/1008731.1008734.
https://doi.org/10.1145/1008731.1008734
[19] Ran Canetti, Yael Tauman Kalai, Mayank Varia, and Daniel Wichs. On symmetric encryption and point obfuscation. In Theory of Cryptography, 7th Theory of Cryptography Conference, TCC 2010, Zurich, Switzerland, February 9-11, 2010. Proceedings, volume 5978 of Lecture Notes in Computer Science, pages 52–71. Springer, 2010. 10.1007/978-3-642-11799-2_4. URL https://www.iacr.org/archive/tcc2010/59780052/59780052.pdf.
https://doi.org/10.1007/978-3-642-11799-2_4
https://www.iacr.org/archive/tcc2010/59780052/59780052.pdf
[20] Kai-Min Chung, Siyao Guo, Qipeng Liu, and Luowen Qian. Tight quantum time-space tradeoffs for function inversion. In 2020 IEEE 61st Annual Symposium on Foundations of Computer Science (FOCS), pages 673–684, 2020. 10.1109/FOCS46700.2020.00068.
https://doi.org/10.1109/FOCS46700.2020.00068
[21] Andrea Coladangelo, Jiahui Liu, Qipeng Liu, and Mark Zhandry. Hidden cosets and applications to unclonable cryptography. In Advances in Cryptology – CRYPTO 2021: 41st Annual International Cryptology Conference, CRYPTO 2021, Virtual Event, August 16–20, 2021, Proceedings, Part I, page 556–584, Berlin, Heidelberg, 2021. Springer-Verlag. ISBN 978-3-030-84241-3. 10.1007/978-3-030-84242-0_20. URL https://doi.org/10.1007/978-3-030-84242-0_20.
https://doi.org/10.1007/978-3-030-84242-0_20
[22] Jan Czajkowski, Christian Majenz, Christian Schaffner, and Sebastian Zur. Quantum lazy sampling and game-playing proofs for quantum indifferentiability. arXiv preprint arXiv:1904.11477, 2019.
arXiv:1904.11477
[23] Edward Eaton and Fang Song. A note on the instantiability of the quantum random oracle. In Jintai Ding and Jean-Pierre Tillich, editors, Post-Quantum Cryptography, pages 503–523, Cham, 2020. Springer International Publishing. ISBN 978-3-030-44223-1. 10.1007/978-3-030-44223-1_27.
https://doi.org/10.1007/978-3-030-44223-1_27
[24] A. Einstein, B. Podolsky, and N. Rosen. Can quantum-mechanical description of physical reality be considered complete? Phys. Rev., 47: 777–780, May 1935. 10.1103/PhysRev.47.777.
https://doi.org/10.1103/PhysRev.47.777
[25] Daniel Gottesman. Uncloneable encryption. Quantum Info. Comput., 3 (6): 581–602, nov 2003. ISSN 1533-7146. 10.26421/QIC3.6-2.
https://doi.org/10.26421/QIC3.6-2
[26] Rishab Goyal, Venkata Koppula, and Brent Waters. Lockable obfuscation. In 2017 IEEE 58th Annual Symposium on Foundations of Computer Science (FOCS), pages 612–621. IEEE, 2017. 10.1109/FOCS.2017.62.
https://doi.org/10.1109/FOCS.2017.62
[27] Dennis Hofheinz, John Malone-Lee, and Martijn Stam. Obfuscation for cryptographic purposes. In Proceedings of the 4th Conference on Theory of Cryptography, TCC’07, page 214–232, Berlin, Heidelberg, 2007. Springer-Verlag. ISBN 9783540709350. 10.1007/978-3-540-70936-7_12.
https://doi.org/10.1007/978-3-540-70936-7_12
[28] Akinori Hosoyamada and Tetsu Iwata. 4-round luby-rackoff construction is a qprp. In Steven D. Galbraith and Shiho Moriai, editors, Advances in Cryptology – ASIACRYPT 2019, pages 145–174, Cham, 2019. Springer International Publishing. ISBN 978-3-030-34578-5. 10.1007/978-3-030-34578-5_6.
https://doi.org/10.1007/978-3-030-34578-5_6
[29] Robert König, Renato Renner, and Christian Schaffner. The operational meaning of min- and max-entropy. IEEE Trans. Inf. Theor., 55 (9): 4337–4347, September 2009. ISSN 0018-9448. 10.1109/TIT.2009.2025545. URL https://doi.org/10.1109/TIT.2009.2025545.
https://doi.org/10.1109/TIT.2009.2025545
[30] Veronika Kuchta, Amin Sakzad, Damien Stehlé, Ron Steinfeld, and Shi-Feng Sun. Measure-rewind-measure: Tighter quantum random oracle model proofs for one-way to hiding and cca security. In Anne Canteaut and Yuval Ishai, editors, Advances in Cryptology – EUROCRYPT 2020, pages 703–728, Cham, 2020. Springer International Publishing. ISBN 978-3-030-45727-3. 10.1007/978-3-030-45727-3_24.
https://doi.org/10.1007/978-3-030-45727-3_24
[31] Jiahui Liu, Qipeng Liu, Luowen Qian, and Mark Zhandry. Collusion resistant copy-protection for watermarkable functionalities. In Theory of Cryptography: 20th International Conference, TCC 2022, Chicago, IL, USA, November 7–10, 2022, Proceedings, Part I, page 294–323, Berlin, Heidelberg, 2022. Springer-Verlag. ISBN 978-3-031-22317-4. 10.1007/978-3-031-22318-1_11. URL https://doi.org/10.1007/978-3-031-22318-1_11.
https://doi.org/10.1007/978-3-031-22318-1_11
[32] Urmila Mahadev. Classical homomorphic encryption for quantum circuits. In Mikkel Thorup, editor, 59th IEEE Annual Symposium on Foundations of Computer Science, FOCS 2018, Paris, France, October 7-9, 2018, pages 332–338. IEEE Computer Society, 2018. 10.1109/FOCS.2018.00039. URL https://doi.org/10.1109/FOCS.2018.00039.
https://doi.org/10.1109/FOCS.2018.00039
[33] Christian Majenz, Christian Schaffner, and Mehrdad Tahmasbi. Limitations on uncloneable encryption and simultaneous one-way-to-hiding, 2021. URL https://arxiv.org/abs/2103.14510.
arXiv:2103.14510
[34] Michael A. Nielsen and Isaac L. Chuang. Quantum Computation and Quantum Information: 10th Anniversary Edition. Cambridge University Press, USA, 10th edition, 2011. ISBN 1107002176. 10.1017/CBO9780511976667.
https://doi.org/10.1017/CBO9780511976667
[35] Oded Regev. On lattices, learning with errors, random linear codes, and cryptography. In Proceedings of the Thirty-Seventh Annual ACM Symposium on Theory of Computing, STOC ’05, page 84–93, New York, NY, USA, 2005. Association for Computing Machinery. ISBN 1581139608. 10.1145/1060590.1060603. URL https://doi.org/10.1145/1060590.1060603.
https://doi.org/10.1145/1060590.1060603
[36] Amit Sahai and Brent Waters. How to use indistinguishability obfuscation: Deniable encryption, and more. SIAM Journal on Computing, 50 (3): 857–908, 2021. 10.1137/15M1030108. URL https://doi.org/10.1137/15M1030108.
https://doi.org/10.1137/15M1030108
[37] Marco Tomamichel, Serge Fehr, Jędrzej Kaniewski, and Stephanie Wehner. A monogamy-of-entanglement game with applications to device-independent quantum cryptography. New Journal of Physics, 15 (10): 103002, 2013. 10.1088/1367-2630/15/10/103002.
https://doi.org/10.1088/1367-2630/15/10/103002
[38] Dominique Unruh. Quantum proofs of knowledge. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pages 135–152. Springer, 2012. 10.1007/978-3-642-29011-4_10.
https://doi.org/10.1007/978-3-642-29011-4_10
[39] Dominique Unruh. Revocable quantum timed-release encryption. J. ACM, 62 (6), December 2015. ISSN 0004-5411. 10.1145/2817206. URL https://doi.org/10.1145/2817206.
https://doi.org/10.1145/2817206
[40] John Watrous. Zero-knowledge against quantum attacks. SIAM Journal on Computing, 39 (1): 25–58, 2009. 10.1137/060670997. URL https://doi.org/10.1137/060670997.
https://doi.org/10.1137/060670997
[41] Daniel Wichs and Giorgos Zirdelis. Obfuscating compute-and-compare programs under lwe. In 2017 IEEE 58th Annual Symposium on Foundations of Computer Science (FOCS), pages 600–611, 2017. 10.1109/FOCS.2017.61.
https://doi.org/10.1109/FOCS.2017.61
[42] Stephen Wiesner. Conjugate coding. SIGACT News, 15 (1): 78–88, January 1983. ISSN 0163-5700. 10.1145/1008908.1008920. URL https://doi.org/10.1145/1008908.1008920.
https://doi.org/10.1145/1008908.1008920
[43] Mark M. Wilde. Quantum Information Theory. Cambridge University Press, USA, 1st edition, 2013. ISBN 1107034256. 10.1017/CBO9781139525343.
https://doi.org/10.1017/CBO9781139525343
[44] A. Winter. Coding theorem and strong converse for quantum channels. IEEE Transactions on Information Theory, 45 (7): 2481–2485, 1999. 10.1109/18.796385.
https://doi.org/10.1109/18.796385
[45] Mark Zhandry. How to construct quantum random functions. In 2012 IEEE 53rd Annual Symposium on Foundations of Computer Science, pages 679–687. IEEE, 2012. 10.1145/3450745.
https://doi.org/10.1145/3450745
[46] Mark Zhandry. Quantum lightning never strikes the same state twice. CoRR, abs/1711.02276, 2017. 10.1007/978-3-030-17659-4_14. URL http://arxiv.org/abs/1711.02276.
https://doi.org/10.1007/978-3-030-17659-4_14
arXiv:1711.02276
[47] Mark Zhandry. How to record quantum queries, and applications to quantum indifferentiability. In Alexandra Boldyreva and Daniele Micciancio, editors, Advances in Cryptology – CRYPTO 2019, pages 239–268, Cham, 2019. Springer International Publishing. ISBN 978-3-030-26951-7. 10.1007/978-3-030-26951-7_9.
https://doi.org/10.1007/978-3-030-26951-7_9
Cited by
[1] Yi-Kai Liu and Dustin Moody, “Post-quantum cryptography and the quantum future of cybersecurity”, Physical Review Applied 21 4, 040501 (2024).
[2] Tony Metger, Alexander Poremba, Makrand Sinha, and Henry Yuen, “Simple constructions of linear-depth t-designs and pseudorandom unitaries”, arXiv:2404.12647, (2024).
[3] John Bostanci, Yuval Efron, Tony Metger, Alexander Poremba, Luowen Qian, and Henry Yuen, “Unitary Complexity and the Uhlmann Transformation Problem”, arXiv:2306.13073, (2023).
[4] Alexandru Gheorghiu, Tony Metger, and Alexander Poremba, “Quantum cryptography with classical communication: parallel remote state preparation for copy-protection, verification, and more”, arXiv:2201.13445, (2022).
[5] Prabhanjan Ananth and Fatih Kaleoglu, “Unclonable Encryption, Revisited”, arXiv:2103.15009, (2021).
[6] Amit Behera and Or Sattath, “Almost Public Quantum Coins”, arXiv:2002.12438, (2020).
[7] Or Sattath and Shai Wyborski, “Uncloneable Decryptors from Quantum Copy-Protection”, arXiv:2203.05866, (2022).
[8] Tony Metger, Alexander Poremba, Makrand Sinha, and Henry Yuen, “Pseudorandom unitaries with non-adaptive security”, arXiv:2402.14803, (2024).
[9] Prabhanjan Ananth, Fatih Kaleoglu, and Qipeng Liu, “Cloning Games: A General Framework for Unclonable Primitives”, arXiv:2302.01874, (2023).
[10] Andrea Coladangelo, Jiahui Liu, Qipeng Liu, and Mark Zhandry, “Hidden Cosets and Applications to Unclonable Cryptography”, arXiv:2107.05692, (2021).
[11] Anne Broadbent, Martti Karvonen, and Sébastien Lord, “Uncloneable Quantum Advice”, arXiv:2309.05155, (2023).
[12] Taiga Hiroka, Tomoyuki Morimae, Ryo Nishimaki, and Takashi Yamakawa, “Quantum Encryption with Certified Deletion, Revisited: Public Key, Attribute-Based, and Classical Communication”, arXiv:2105.05393, (2021).
[13] Anne Broadbent, Stacey Jeffery, Sébastien Lord, Supartha Podder, and Aarthi Sundaram, “Secure Software Leasing Without Assumptions”, arXiv:2101.12739, (2021).
[14] Prabhanjan Ananth, Alexander Poremba, and Vinod Vaikuntanathan, “Revocable Cryptography from Learning with Errors”, arXiv:2302.14860, (2023).
[15] Prabhanjan Ananth, Zihan Hu, and Henry Yuen, “On the (Im)plausibility of Public-Key Quantum Money from Collision-Resistant Hash Functions”, arXiv:2301.09236, (2023).
[16] Anne Broadbent and Eric Culf, “Uncloneable Cryptographic Primitives with Interaction”, arXiv:2303.00048, (2023).
[17] James Bartusek, Fuyuki Kitagawa, Ryo Nishimaki, and Takashi Yamakawa, “Obfuscation of Pseudo-Deterministic Quantum Circuits”, arXiv:2302.11083, (2023).
[18] Alex B. Grilo, Kathrin Hövelmanns, Andreas Hülsing, and Christian Majenz, “Tight adaptive reprogramming in the QROM”, arXiv:2010.15103, (2020).
[19] Prabhanjan Ananth and Fatih Kaleoglu, “A Note on Copy-Protection from Random Oracles”, arXiv:2208.12884, (2022).
[20] Fuyuki Kitagawa and Ryo Nishimaki, “One-out-of-Many Unclonable Cryptography: Definitions, Constructions, and More”, arXiv:2302.09836, (2023).
[21] Shweta Agrawal, Fuyuki Kitagawa, Ryo Nishimaki, Shota Yamada, and Takashi Yamakawa, “Public Key Encryption with Secure Key Leasing”, arXiv:2302.11663, (2023).
[22] Christian Majenz, Maris Ozols, Christian Schaffner, and Mehrdad Tahmasbi, “Local simultaneous state discrimination”, arXiv:2111.01209, (2021).
The above citations are from SAO/NASA ADS (last updated successfully 2024-05-03 23:10:42). The list may be incomplete as not all publishers provide suitable and complete citation data.
On Crossref’s cited-by service no data on citing works was found (last attempt 2024-05-03 23:10:40).
This Paper is published in Quantum under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. Copyright remains with the original copyright holders such as the authors or their institutions.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://quantum-journal.org/papers/q-2024-05-02-1330/
- :is
- :not
- 07
- 1
- 10
- 10th
- 11
- 12
- 1222
- 13
- 14
- 15%
- 15th
- 16
- 17
- 19
- 1999
- 1st
- 2%
- 20
- 2005
- 2007
- 2009
- 2010
- 2011
- 2012
- 2013
- 2015
- 2016
- 2017
- 2018
- 2019
- 2020
- 2021
- 2022
- 2023
- 2024
- 20th
- 21
- 22
- 23
- 24
- 24th
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35%
- 36
- 39
- 4
- 40
- 41
- 42
- 45
- 46
- 4th
- 5
- 50
- 51
- 55
- 6
- 62
- 7
- 7th
- 8
- 9
- a
- Able
- above
- ABSTRACT
- access
- Achieve
- Achieves
- ACM
- adaptive
- advances
- ADvantage
- adversarial
- advice
- affiliations
- against
- alex
- Alexander
- alexandra
- All
- allows
- almost
- and
- andrea
- Anniversary
- annual
- any
- Application
- applications
- applied
- approaches
- arbitrary
- ARE
- AS
- Association
- assumptions
- At
- Attacks
- attempt
- AUGUST
- Authentication
- author
- authors
- b
- BE
- because
- Berkeley
- berlin
- between
- Bill
- Black-box
- both
- bound
- Break
- brent
- by
- california
- called
- cambridge
- CAN
- cannot
- captures
- ccc
- Certified
- channels
- Charles
- chicago
- Chris
- christian
- circuits
- citing
- class
- Codes
- Coding
- Coins
- collusion
- comment
- Commons
- Communication
- Communications
- complementary
- complete
- complexity
- computation
- computational
- computer
- computer science
- computing
- Conference
- conjugate
- considered
- construct
- construction
- constructions
- contribution
- copies
- copying
- copyright
- could
- create
- crypto
- cryptographic
- cryptography
- Cybersecurity
- damien
- dan
- Daniel
- data
- December
- definitions
- Den
- Denmark
- description
- designing
- Discrimination
- discuss
- distributor
- does
- e
- edition
- editor
- editors
- Edward
- efficient
- einstein
- encryption
- enjoy
- Equivalent
- eric
- Errors
- ethan
- Ether (ETH)
- evaluated
- Event
- expressive
- feasibility
- Features
- February
- fhe
- Finally
- First
- following
- For
- formal
- found
- Foundations
- Framework
- France
- from
- fully
- function
- functionalities
- functionally
- functions
- future
- game
- Games
- General
- Germany
- Gilles
- hamburg
- harvard
- hash
- henry
- Hidden
- hiding
- High
- holders
- homomorphic
- How
- How To
- However
- http
- HTTPS
- i
- IEEE
- if
- image
- impossible
- in
- info
- information
- information security
- initiated
- input
- inputs
- institutions
- interaction
- interesting
- International
- introduce
- introduced
- inversion
- IT
- ITS
- james
- Jan
- January
- JavaScript
- John
- journal
- July
- Key
- Kind
- knowledge
- known
- König
- la
- large
- Last
- learning
- leasing
- least
- Leave
- Lecture
- Level
- li
- License
- lightning
- limitations
- linear
- List
- local
- lord
- machinery
- MAKES
- malicious
- Marco
- mark
- mathematical
- mathematics
- max-width
- May..
- meaning
- message
- Methodology
- Michael
- mike
- model
- money
- Month
- more
- naive
- Netherlands
- never
- New
- New York
- news
- no
- note
- Notes
- Notion
- notions
- nov
- November
- NY
- october
- of
- offer
- on
- open
- operational
- or
- oracle
- Oracles
- original
- otherwise
- our
- output
- outputs
- page
- pages
- Paper
- paradigm
- Parallel
- paris
- part
- physical
- Physics
- plato
- Plato Data Intelligence
- PlatoData
- Point
- possibility
- possible
- Practical
- preparation
- press
- prevents
- primitives
- principle
- Problem
- Proceedings
- Program
- Programs
- proofs
- protection
- protocols
- provable
- Prove
- provide
- public
- Public Key
- published
- publisher
- publishers
- Publishing
- purposes
- Quantum
- quantum computing
- quantum cryptography
- quantum information
- queries
- ran
- random
- range
- Reality
- realm
- receives
- recently
- record
- references
- relationship
- remains
- remote
- resistant
- result
- review
- ROBERT
- RON
- Run
- s
- same
- satisfies
- satisfy
- scheme
- schemes
- Science
- SCIENCES
- scott
- scott aaronson
- sebastian
- Second
- secure
- security
- seems
- September
- setting
- should
- show
- siam
- Simple
- simply
- simultaneous
- Society
- Software
- solution
- song
- specified
- standard
- State
- Stephen
- steven
- Strategy
- strengths
- Strikes
- String
- strong
- Study
- Successfully
- such
- suitable
- Sun
- switzerland
- Symposium
- T
- Task
- Technical
- techniques
- thanks
- that
- The
- the Netherlands
- their
- theorem
- theory
- they
- Third
- this
- tighter
- Title
- to
- Tony
- tradeoffs
- trans
- Transactions
- Transformation
- Twice
- under
- university
- updated
- URL
- USA
- use
- User
- using
- vendor
- Verification
- very
- via
- Virtual
- volume
- want
- was
- Waters
- Way..
- we
- weaker
- weaknesses
- which
- while
- WHO
- Winter
- wishes
- with
- within
- without
- Work
- working
- works
- world
- X
- year
- yet
- york
- zephyrnet
- zero-knowledge
- zhang
- Zurich